Dark Market Honeypot: A Tool for Ethical Hackers to Track Black Hats
PROJECTS


Introduction
In cybersecurity, honeypots serve as powerful tools for luring malicious actors into revealing their methods and identities. Today, I'm excited to introduce a honeypot I developed, called "Dark Market." This honeypot is designed to mimic an illegal marketplace, providing ethical hackers with a unique opportunity to track black hats by capturing crucial data during their interactions.
What is the Dark Market Honeypot?
The Dark Market honeypot is a Flask-based web application that simulates a dark market environment where users can "purchase" various illegal goods such as hacking courses, drugs, firearms, and stolen credit card information. However, instead of enabling these transactions, the honeypot captures and logs the user's IP address, browser details, and even login credentials, providing ethical hackers with valuable information to track down and analyze potential black hats.
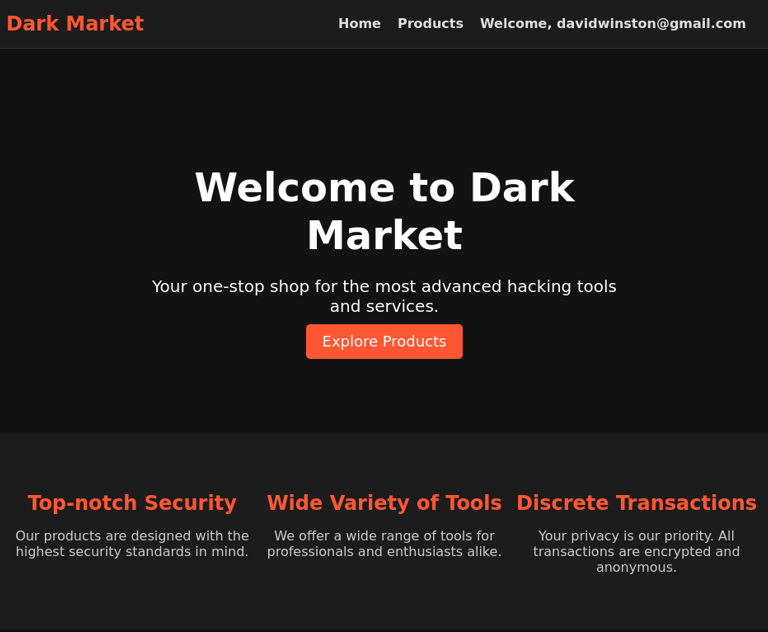
Homepage of the Dark Market
When a user visits the Dark Market honeypot, they are greeted with a homepage. This page is designed to look as realistic as possible to entice malicious actors into interacting with the site.
VPN Detection - User Denied Entry
One of the honeypot's key security features is its ability to detect if a user is using a VPN. The honeypot leverages an API to identify VPN usage. If a VPN is detected, the user is denied entry and prompted to disable it. This feature helps ensure that the honeypot captures more accurate information about the user's true location and identity.
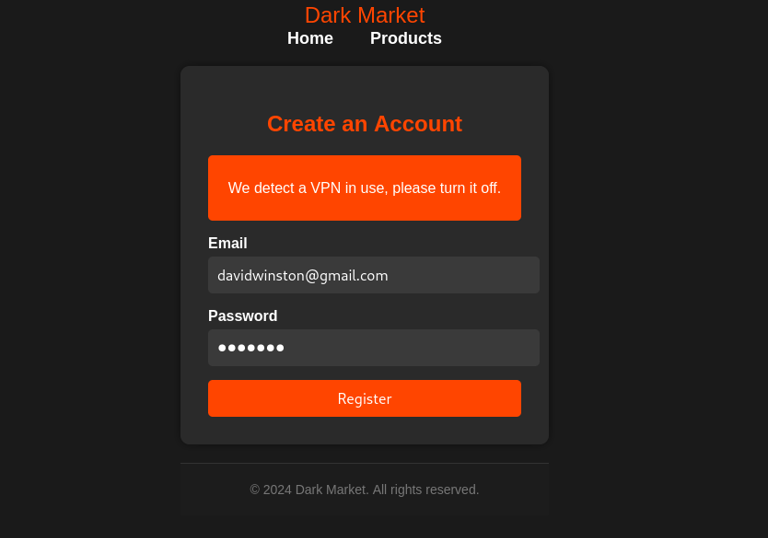
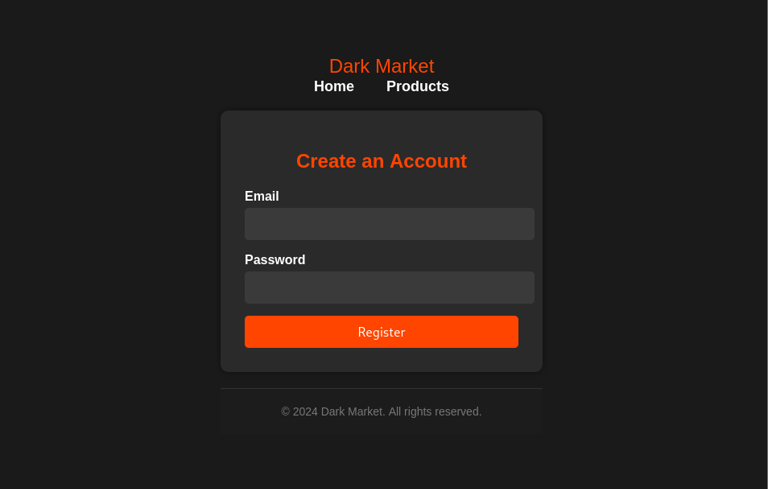
Registration Page
Before accessing any content on the Dark Market, users are required to register. This step is crucial as it allows the honeypot to log important details such as the user's IP address, email, and browser information from the very beginning of their interaction with the site.
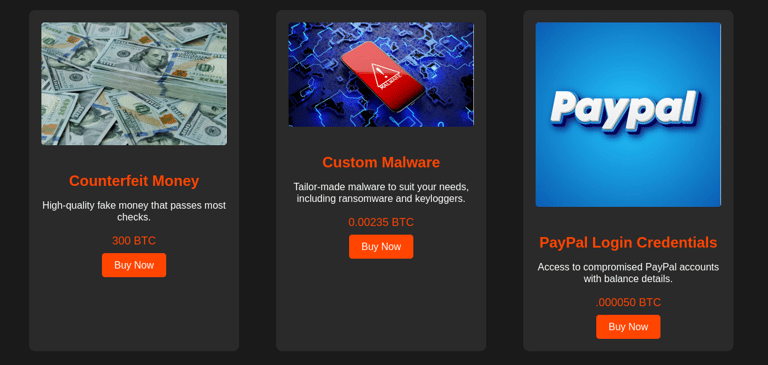
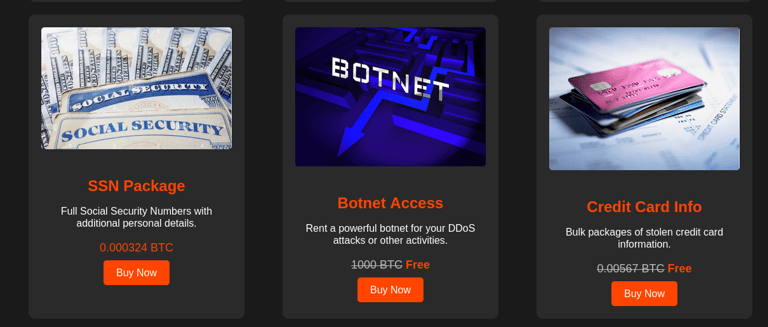
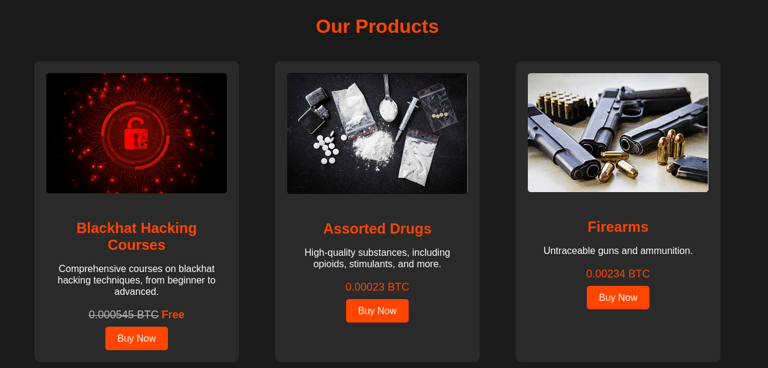
Products Page
Once registered, users are directed to the products page. Here, they can browse through a range of illicit items, including hacking courses, drugs, firearms, and more. Each product is presented with detailed descriptions, Bitcoin pricing, and images to enhance the authenticity of the dark market experience.

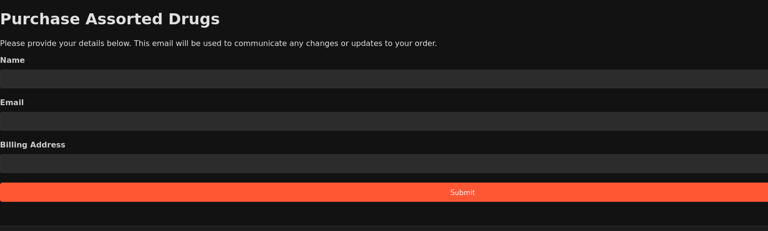
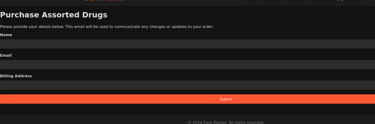
Purchase Attempt Form
When a user attempts to "purchase" a product, they are presented with a form to fill out their personal details, including their name, email, and billing address. This information, along with their IP address and browser details, is logged for further analysis. This step simulates a real purchasing process on a dark market, adding depth to the honeypot’s realism.
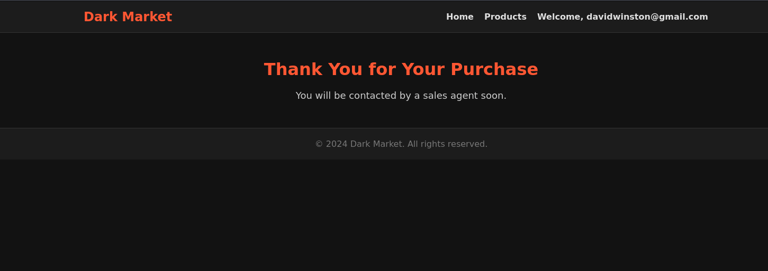
Purchase Confirmation Page
After submitting the purchase form, the user is redirected to a confirmation page. This adds an extra layer of realism to the honeypot, simulating a complete transaction process that could occur on an actual dark market site.
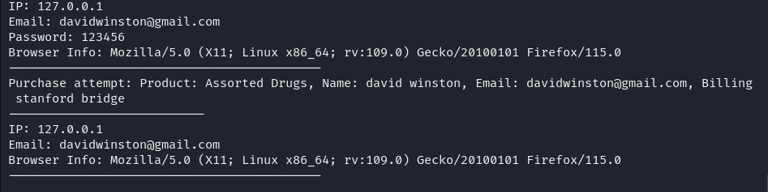
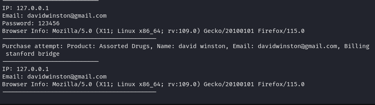
Logs Overview
Behind the scenes, every interaction on the site is meticulously recorded in log files. These logs capture critical information, including IP addresses, email addresses, browser details, and specific actions taken by the user. This data is crucial for ethical hackers, enabling them to track, analyze, and understand the behavior of potential black hats
Deployment and Usage
The Dark Market honeypot is easy to deploy on any server running Flask. Once live, it becomes a magnet for black hat hackers who believe they are accessing a real dark market. Ethical hackers can then analyze the logged data to gain insights into the methods and tactics employed by these malicious actors.
Conclusion
The Dark Market honeypot is a powerful tool for ethical hackers to gather intelligence on black hats. By creating a convincing environment that mimics a dark market, this honeypot allows ethical hackers to monitor, analyze, and ultimately understand the tactics used by malicious actors. As cyber threats continue to evolve, tools like this honeypot play a critical role in maintaining the upper hand in the ongoing battle against cybercrime.
Ready to deploy your own honeypot? Follow the steps outlined in this blog, and you'll be on your way to setting up a powerful tool to track black hats in no time.
