Cybercriminals Weaponizing Open-Source SSH-Snake Tool for Network Attacks
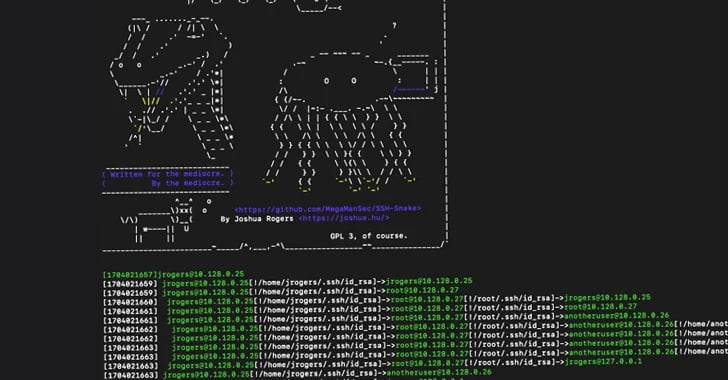
A network mapping tool called SSH-Snake, recently made open-source, has been repurposed by threat actors for malicious activities. According to Sysdig researcher Miguel Hernández, SSH-Snake is a self-modifying worm that uses SSH credentials found on a compromised system to spread across the network. It automatically searches for credentials and shell history files to determine its next move.
BLOGS
A network mapping tool called SSH-Snake, recently made open-source, has been repurposed by threat actors for malicious activities.
According to Sysdig researcher Miguel Hernández, SSH-Snake is a self-modifying worm that uses SSH credentials found on a compromised system to spread across the network. It automatically searches for credentials and shell history files to determine its next move.
Initially released on GitHub in January 2024, SSH-Snake is described by its developer as a tool to automatically traverse networks using SSH private keys discovered on systems. It maps out the network and its dependencies, helping assess the potential compromise of a network starting from a specific host, even resolving domains with multiple IP addresses.
The tool is fileless and self-replicating, making it more stealthy and flexible than typical SSH worms, as noted by Sysdig. It has been observed in real-world attacks, harvesting credentials, IP addresses, and bash command history following the discovery of a command-and-control (C2) server.
Threat actors deploy SSH-Snake by actively exploiting known security vulnerabilities in Apache ActiveMQ and Atlassian Confluence instances to gain initial access and spread the worm.
Joshua Rogers, the developer of SSH-Snake, stated that the tool can be used by system owners to identify weaknesses in their infrastructure before attackers do. He emphasized the importance of comprehensive security measures and infrastructure design to minimize the impact of such attacks.
The disclosure coincides with the discovery of a new botnet campaign named Lucifer, which exploits misconfigurations and flaws in Apache Hadoop and Apache Druid to mine cryptocurrency and launch distributed denial-of-service (DDoS) attacks.
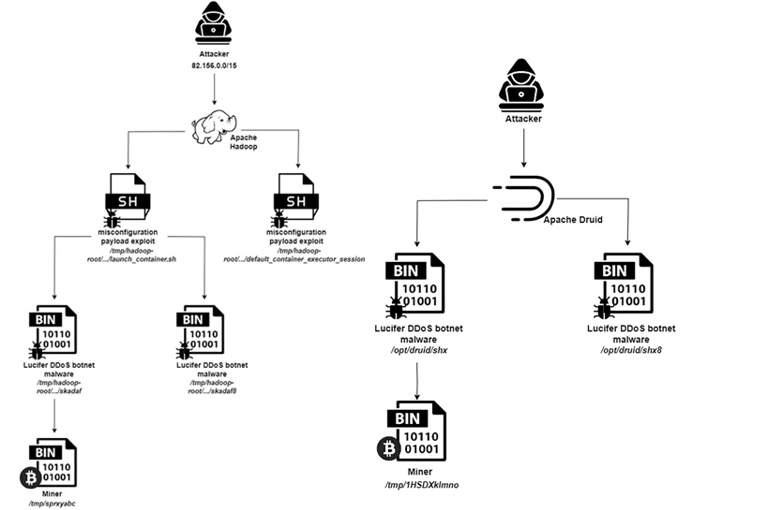
Over the past month, approximately 3,000 distinct attacks targeting the Apache big data stack have been identified, including those specifically targeting vulnerable Apache Flink instances to deploy miners and rootkits, according to the cloud security firm.
Security researcher Nitzan Yaakov explained that attackers exploit existing misconfigurations and vulnerabilities in these services to carry out the attacks.
Given the widespread use of Apache open-source solutions by numerous users and contributors, attackers may see this as an opportunity to exploit a vast pool of resources for their malicious activities.
