CL0P's Ransomware Rampage - Security Measures for 2024
BLOGS


2023 CL0P Growth
In early 2019, CL0P emerged as a more sophisticated iteration of the 'CryptoMix' ransomware, introduced by the CL0P ransomware organization. Initially active, the group continued its operations with notable campaigns spanning from 2020 to 2022. However, in 2023, the CL0P ransomware gang elevated its activities to unprecedented levels, establishing itself as one of the most prominent and successful ransomware groups globally.
Exploiting numerous vulnerabilities and exploits, particularly within some of the world's largest organizations, the presumed Russian gang adopted its name from the Russian term "klop," meaning "bed bug," often depicted as "CLOP" or "cl0p." Upon encrypting victims' files, ".clop" extensions were appended to denote the compromise.
CL0P's Methods & Tactics
The CL0P ransomware gang, closely linked with cybercrime groups TA505, FIN11, and UNC2546, gained notoriety for its highly destructive and aggressive campaigns targeting large organizations worldwide throughout 2023. Operating as a "big game hunter" ransomware group, CL0P employed the "steal, encrypt, and leak" strategy, particularly targeting companies in the Finance, Manufacturing, and Healthcare sectors.
CL0P adopted a Ransomware-as-a-Service (RaaS) model, commonly utilizing the 'steal, encrypt, and leak' tactics prevalent among ransomware affiliates globally. In cases where victims failed to meet ransom demands, their data was publicly disclosed via the gang's Tor-hosted leak site, 'CL0P^_-LEAKS'. Similar to many other Russian-speaking cyber gangs, CL0P's ransomware was ineffective on devices located within the Commonwealth of Independent States (CIS).
Similarly, LockBit operated on an RaaS model, wherein affiliates made a deposit to access the tool and split the ransom payment with the LockBit group. Reports indicated that some affiliates received up to a 75% share. LockBit's operators advertised their affiliate program on Russian-language criminal forums, specifying their avoidance of operations in Russia, CIS countries, and collaborations with English-speaking developers without a Russian-speaking "guarantor." This information was detailed in 'The Prolificacy of LockBit Ransomware'.
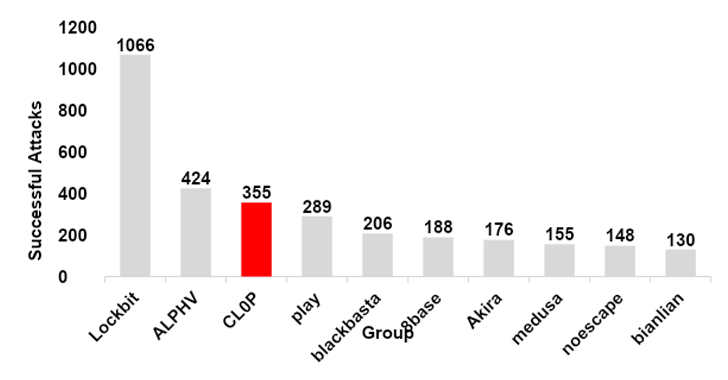
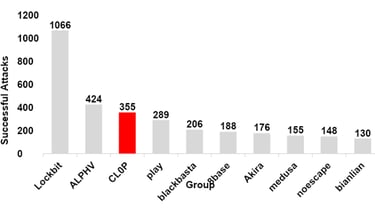
3rd Most Prolific Group 2023
After examining the data from 'CL0P^_-LEAKS', the threat intelligence team at SecurityHQ was able to collect data on various cybercrime gangs around the world and help visualize the extent of CL0P's rise in activity throughout 2023. The gangs' transition from remaining outside the topmost active ransomware groups in 2022 to securing the third most prolific in 2023 is something that should not be taken lightly.
Latest Activities
Throughout March 2023, the CL0P ransomware gang made attempts to exploit a zero-day vulnerability in 'Fortra GoAnywhere MFT', tracked as CVE-2023-0669. By targeting unpatched versions of the software accessible via the internet, attackers successfully achieved Remote Code Execution (RCE), impacting over 100 organizations before the vulnerability was patched the following day.
In April, Microsoft identified the involvement of two ransomware groups, CL0P and LockBit, exploiting CVE-2023-27350 and CVE-2023-27351 within the print management software PaperCut. This software is widely used among large printing firms globally. The groups leveraged this vulnerability to deploy the notorious TrueBot malware, shifting tactics from mere file encryption to data theft for further extortion. The inclusion of PaperCut's "Print Archiving" tool facilitated data capture for exploitation.
May marked a significant event for the group as they actively exploited CVE-2023-24362 in MOVEit Transfer and CVE-2023-35036 in MOVEit Cloud Software, utilizing an unknown SQL injection vulnerability. CL0P swiftly capitalized on vulnerable networks, extracting sensitive data from prominent organizations such as BBC, Ernst Young, PwC, Gen Digital, British Airways, TFL, Siemens, among others. Although the group claimed to have deleted data concerning governments, military, and hospitals, the breach's impact on several US government agencies prompted a $10 million bounty, raising concerns of potential foreign involvement.
Lasting Impact of Quadruple Extortion
The group has played a significant role in the surge of ransomware activity throughout 2023 and has notably contributed to a considerable increase in average ransom payments.
CL0P's operators are infamous for their relentless pursuit of their objectives. If their messages and proofs of breach on their leak site are disregarded, they escalate to directly contacting stakeholders and executives to ensure compliance, a tactic known as quadruple extortion.
Ransomware groups have progressed from single to double, then to triple extortion, and now to quadruple extortion, demonstrating their persistent pursuit of their goals. Quadruple extortion introduces two primary tactics:
1. DDoS attacks aim to disrupt an organization's online operations until the ransom is paid.
2. The harassment of various stakeholders, including customers, media, and employees, intensifies pressure on decision-makers to meet the ransom demands.
Best Defense Against CL0P Group Defending Against CL0P
To effectively defend against CL0P in 2024, SecurityHQ recommends:
1. Maintain vigilance over your environment and landscape. Understand what constitutes normal activity within your environment to swiftly identify anomalies and respond promptly.
2. Develop and regularly review your Incident Response Plan, outlining clear steps to follow in worst-case scenarios to ensure swift and coordinated actions.
3. Implement robust Threat Monitoring capabilities to swiftly detect and respond to potential threats.
4. Regularly assess and enhance your current cybersecurity practices to ensure alignment with industry best practices.
5. Individuals or organizations at higher risk, particularly those in industries targeted by CL0P such as Finance, Manufacturing, and Healthcare, or those holding sensitive data, should consider partnering with a Managed Security Service Provider (MSSP) to ensure the implementation of top-tier security measures.
Threat Intelligence for the Future
SecurityHQ's Threat Intelligence team operates as a unified global entity dedicated to Cyber Threat Intelligence. Their primary focus is on researching emerging threats and monitoring the activities of threat actors, ransomware groups, and campaigns to proactively identify potential risks. In addition to their investigative efforts, the Intelligence team offers actionable threat intelligence and research, enriching the knowledge of SecurityHQ's clients worldwide. Bound by a shared commitment, the SecurityHQ Threat Intelligence team provides the necessary insights to navigate the complexities of the cybersecurity threat landscape with confidence.
For further information on these threats, consult with an expert here. If you suspect a security incident, you can report it here.
