Chinese-Linked LightSpy iOS Spyware Targets South Asian iPhone Users
BLOGS


Cybersecurity analysts have detected a renewed cyber espionage operation targeting individuals in South Asia, aiming to deploy an Apple iOS spyware tool known as LightSpy.
Described as 'F_Warehouse,' the latest version of LightSpy features a modular framework equipped with extensive surveillance capabilities, according to a recent report by the BlackBerry Threat Research and Intelligence Team.
Evidence suggests that the campaign may have specifically focused on India, based on VirusTotal submissions originating from within the country.
Originally identified in 2020 by Trend Micro and Kaspersky, LightSpy represents a sophisticated iOS backdoor distributed through watering hole attacks, typically exploiting compromised news websites.
In October 2023, further investigation by ThreatFabric revealed infrastructure and functionality similarities between LightSpy and an Android spyware called DragonEgg, associated with the Chinese state-sponsored group APT41 (also known as Winnti).
Although the initial method of intrusion remains unclear, it is suspected to involve compromised news sites frequented by the targeted individuals.
The attack begins with a first-stage loader serving as a launching pad for the core LightSpy backdoor and various plugins, retrieved from a remote server to execute data collection operations.
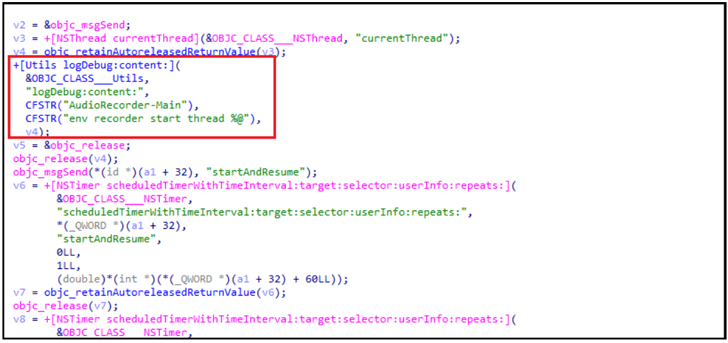
"LightSpy is a comprehensive and adaptable tool, empowering malicious actors to extract sensitive data such as contacts, SMS messages, precise location coordinates, and audio recordings from VoIP calls.
The latest iteration identified by a Canadian cybersecurity company extends its reach to pilfering files and information from popular apps like Telegram, QQ, and WeChat, along with iCloud Keychain data and browsing history from Safari and Google Chrome.
This intricate surveillance framework also boasts the ability to compile a list of connected Wi-Fi networks, collect data on installed applications, capture images using the device's camera, record audio, and execute commands remotely, potentially granting full control over compromised devices.
"LightSpy utilizes certificate pinning to thwart detection and interception of communications with its command-and-control (C2) server," as stated by Blackberry. "Therefore, even if the victim's network traffic is under scrutiny, it won't establish a connection with the C2 server."
A closer analysis of the implant's source code hints at the involvement of native Chinese speakers, hinting at possible state-sponsored activity. Additionally, LightSpy communicates with a server located at 103.27[.]109[.]217, hosting an admin panel that displays Chinese error messages for incorrect login attempts.
This development coincides with Apple issuing threat notifications to users in 92 countries, including India, warning of potential targeting by mercenary spyware attacks.
"The resurgence of LightSpy, now featuring the versatile 'F_Warehouse' framework, marks an escalation in mobile espionage threats," remarked BlackBerry.
"The enhanced capabilities of this malware, encompassing extensive data theft, audio surveillance, and potential device takeover, pose a significant danger to targeted individuals and organizations across Southern Asia."
