Building Your Own Python Backdoor: A Comprehensive Guide
ARTICLES
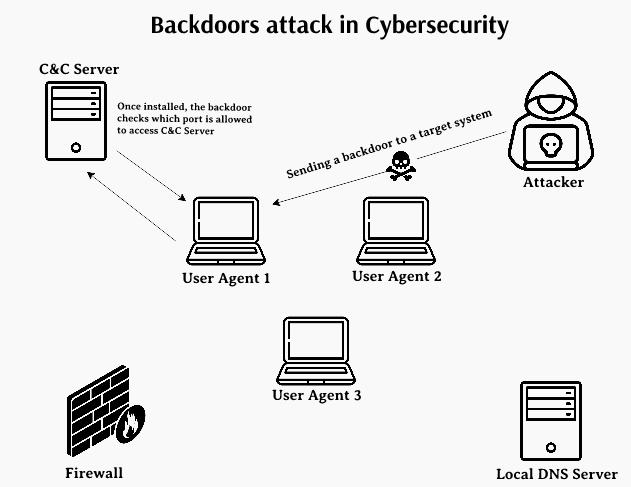
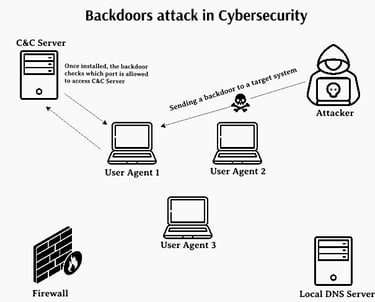
In cybersecurity, understanding offensive techniques like backdoors is essential for developing strong defenses. This guide explains how to create a simple Python-based backdoor system with a client (victim) and a server (attacker).
What is a Backdoor?
A backdoor is a malicious tool that allows attackers to bypass normal authentication and access a system remotely. Backdoors are often used to control compromised machines, execute commands, or exfiltrate data.
Today our demonstration will involve:
Server (Attacker): A script that listens for incoming connections and sends commands.
Client (Victim): A script running on the victim's system, connecting back to the attacker to execute commands.
Components of the Backdoor
The backdoor has two primary components:
Server Component: Initiates control by listening for client connections and sending commands.
Client Component: Executes commands received from the server and returns the output.
1. Server Script (Attacker)
The server represents the attacker’s machine. It:
Listens for incoming client connections.
Sends commands to the connected client.
Displays the results of those commands.
2. Client Script (Victim)
The client represents the victim’s machine. It:
Connects to the attacker’s server.
Waits for commands from the server.
Executes the commands and returns the output.
Step-by-Step Explanation
1. Server (Attacker) Workflow
Creating the Server Socket:
bind(): Assigns an IP and port for the server.
listen(): Prepares the server to accept incoming connections.
Accepting a Connection:
Waits for a client to connect.
Prints the client’s IP address and port.
Sending and Receiving Data:
Commands are sent to the client using:
Responses are received using
The connection closes when the command exit is sent.
2. Client (Victim) Workflow
Connecting to the Server:
The client connects to the attacker’s IP and port.
Receiving and Executing Commands:
Commands are received via:
Commands are executed using the subprocess module:
Errors during execution are handled using try-except.
Sending Results Back:
The executed command’s output or errors are sent back to the server.
How to Test the Backdoor
Run the Server:
Open a terminal on the attacker’s machine.
Run the server script.
Run the Client:
Execute the client script on a different machine (or VM).
Ensure that the REMOTE_HOST and REMOTE_PORT in the client script match the server’s details.
Send Commands:
Type commands into the server’s terminal (e.g., whoami, dir/ls, ipconfig/ifconfig).
Observe the results returned by the client.
