Building an ATM Skimmer for Educational Purposes
PROJECTSBLOGS


When most people hear the term skimmer, they immediately think of credit card fraud and identity theft. But for cybersecurity professionals and ethical hackers, understanding how these tools work is essential — not just to exploit, but to defend. That’s why I created a fully functioning ATM skimmer system: not to steal data, but to teach students the reality behind skimming attacks.
With the help of a friend, I combined a real payment terminal (purchased online) with a custom-built web-based dashboard to track and manage skimmed card data.
How I Built It
I started by purchasing a payment terminal from Amazon — the kind you’d find at a store checkout. This device was then modified to act as a skimmer, capturing the card number, CVV, expiration date, and other basic info when a card is swiped or inserted.
With my friend’s help, we connected the skimmer to a custom web interface that logs every card interaction and gives a real-time overview of everything happening. This dashboard acts as the “attacker’s control panel” — just like what a real-world cybercriminal might use, except ours is fully safe AND JUST FOR DEMONSTRATION.
The Dashboard — A Look Inside
The dashboard includes the following sections:
✅ Cards View
This shows a list of all captured cards, including:
Card Number
Cardholder Name
Balance
CVV
Expiration
Bank
Location (State)
Type (Credit/Debit)
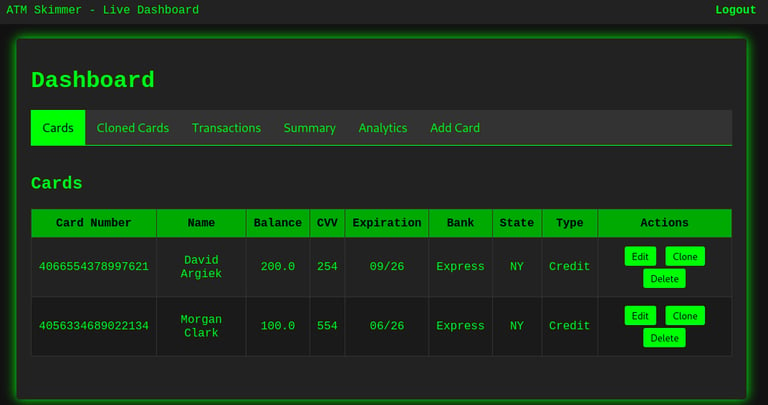
Actions available include Edit, Clone, or Delete — simulating what a real attacker might do with captured card data.
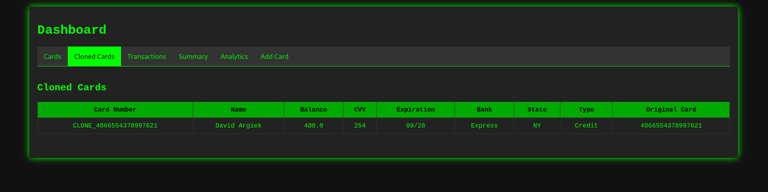
Cloned Cards Section – Managing Duplicates
The Cloned Cards tab is where duplicated card entries are tracked. This is important because in the real world, attackers will clone cards onto fake magnetic stripes or NFC chips for ATM withdrawals or in-person fraud.
This feature shows students how easy it is to manage cloned copies of a single victim's card, and how this is often used to avoid triggering bank detection systems (by spreading out fraudulent charges).
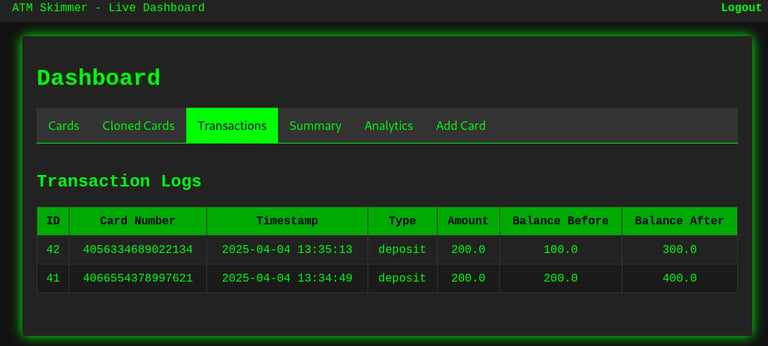
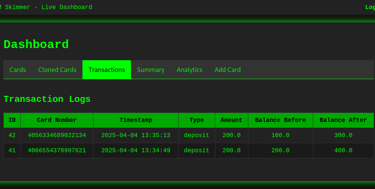
Transactions Section – Monitor All Activity
One of the most powerful parts of the tool is the Transactions section. Every time a card is used — whether for a deposit, withdrawal, or balance change — it's logged here with:
Timestamp
Card Number
Type of Action (Deposit/Withdraw)
Amount
Balance Before and After
This teaches students how card fraud rings monitor transactions in real time to avoid overdrawing cards or drawing suspicion. It also shows how they track which cards are "live" and which are "burned."
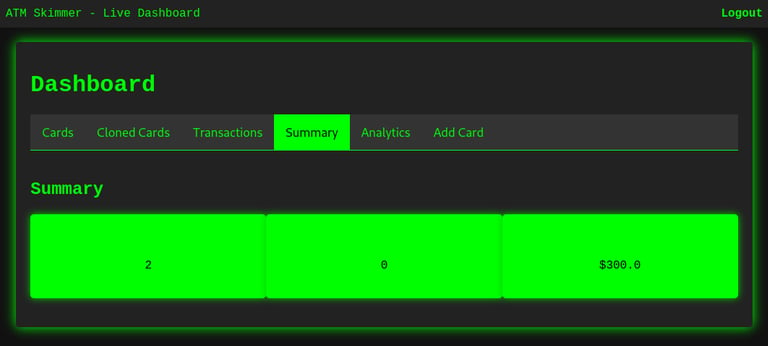
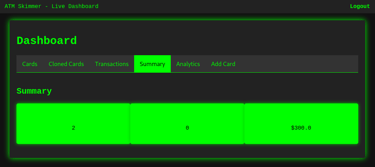
Summary Section – Overview of Assets
The Summary tab provides an instant snapshot of:
Total number of cards
Number of cloned cards
Total balance across all stored cards
This helps students understand how attackers track the total potential profit from a batch of skimmed data — and prioritize which cards to act on.
Add Card Section – Manual Data Entry
Not every attacker relies on automatic skimming. In many cases, criminals receive card dumps from other sources and enter them manually into their databases. The Add Card tab allows for this, with fields for:
Card Number
Name
Balance
CVV
Expiration Date
Bank
State
Card Type
This feature lets students experiment with mock data and see how each new card behaves in the dashboard.
Why I Built This (And Why It Matters)
This system wasn’t made to steal data — it was made to show the process. Too often, cybersecurity courses focus only on the defensive side. But when you can sit down with students and say, “Here’s how an attacker actually sees your card,” — the learning hits harder.
By showing them:
What stolen card data looks like
How it's managed and tracked
How cloned cards are used and monitored
How a single terminal can feed a live dashboard in real time
...students gain the knowledge they need to think like an attacker — and defend like a pro.
Skimming isn't just theory. It's real. And now, my students get to see it for what it is — safely, legally, and up close.
