Brute Force Attack on Web Forms
HACKING-TUTORIALS


In this guide, we will learn how to brute force a web form using THC-Hydra. We will be using a wordlist that has been generated using the Crunch utility. Using Burp Suite and THC-Hydra we will be to automate a brute force attack on a login form.
In this guide, we will be using the Damn Vulnerable Web Application.
Requirements
PC running Kali Linux.
Target web form (We will attack the Damn Vulnerable Web App login form).
Burp Suite.
THC-Hydra.
DVWA
In this guide, we will be bypassing the login page of the Damn Vulnerable Web Application. We will be using the dockerized version of DVWA but you can also install DVWA application manually.
After downloading and extracting is complete, we can run the instance using the command.
After the container is up, we can access the DVWA login form using the docker IP address http://<ipaddress>/login.php. In the image below, we have the form we will be performing a brute force attack on.


Burp Suite
Using Burp Suite we will capture the login link and the parameters which we will be using for brute forcing the login form on the next step using THC-Hydra. On Burp Suite we want to use the proxy tool. On our favorite web browser, we configure the proxy tunneling to capture the request made on the target website.
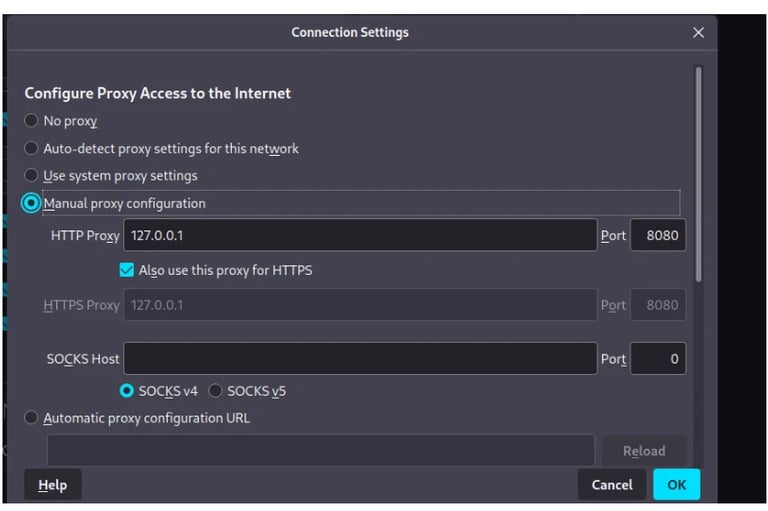
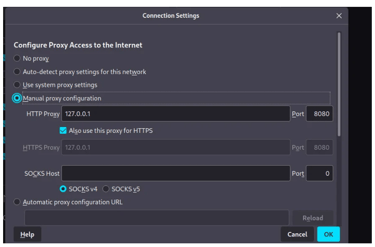
After the configuration is ready, we can navigate to the DVWA login page and try to log in with random credentials. We will be capturing the POST request sent to the server and the string that has the login credentials as shown in the image below.
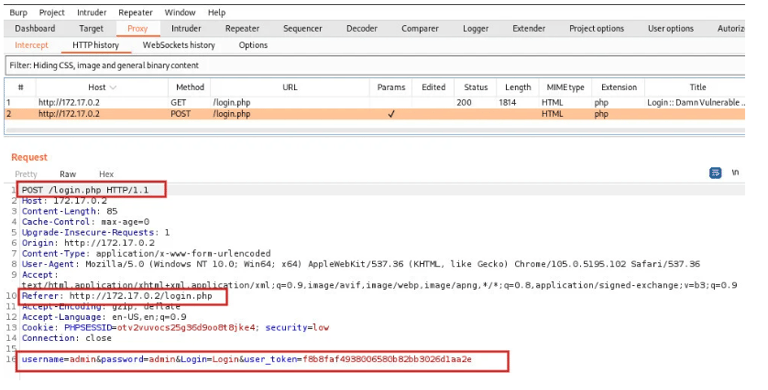
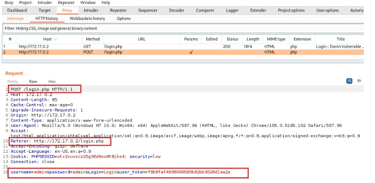
After submitting the wrong login credentials, a “login failed” notice appears on the login page. We need this “login failed” notice while we are brute forcing the login form.


We now have the needed information to start a brute force attack.
THC-Hydra
THC-Hydra is a network logon cracker that has support for numerous services. It is also very fast when cracking login credentials. Some of the advantages of using THC-Hydra include;
Supports various protocols. i.e. POP3, HTTP-GET, HTTP-FORM POST, Telnet, Firebird e.t.c.
You can perform parallel dictionary attacks.
Helps avoid detection by Intrusion Prevention Systems through various processes. i.e. slows down the brute force attack by adding a wait time between each attempt.
THC-Hydra checks for reversed, null, and even usernames and passwords.
Installation
THC-Hydra comes pre-installed on Kali Linux. In a case where THC-Hydra is not installed, we can install it by cloning it from the official GitHub repository.
We then navigate to the downloaded folder and run the installation.
Brute force attack on login form using THC-Hydra
Having the required details to start brute forcing login form. There are several parameters we need to provide in order to launch the attack. Some of the options that can be used with THC-Hydra.
-l- used to indicate a single username (for a list we will use -L).
-P -used to indicate password list to use.
http-post-form- used to indicate the type of form.
/login.php - is the login page URL.
username- This is the form field where the username will be entered.
^USER^- tells Hydra to use the username or list provided in the field.
password- This is the form field where the password is entered (it can be pass or passwd).
^PASS^ - This tells Hydra to use the password list provided.
Login- indicates to Hydra the login failed message.
Login failed - is the login failure message that the form returned.
-V- is for verbose output showing every attempt.
The command syntax we will use to launch the attack
In our attack, we will be using the below syntax.
We first need to have a word list and a password list which we will use when brute forcing the login page. We will use Crunch as we had learned in an earlier guide to generating the lists required. After we generate the lists we require, we can now point their locations in the command and launch the attack as shown in the image below.
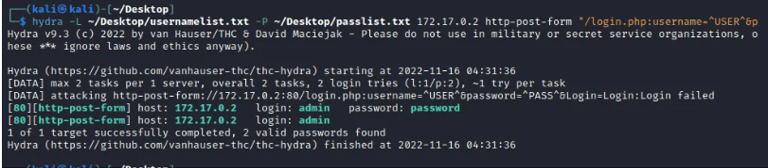
THC-Hydra will try to bypass the login page using the credentials provided in the word list and password list.
As a penetration tester, you may come across web login forms that have limited number of login trials within a specified period. THC-Hydra provides us with an option to allow it to sleep and wait when the maximum attempts are reached and resume when the time has elapsed.
Conclusion
In the above guide, we were able to learn how to perform a brute force attack on an online form. THC-Hydra was used to automate the brute force attack saving the time and effort used on such a tedious task. We can use THC-Hydra for automated brute forcing of online login forms. The tool can also be used on other kinds of brute force attacks during a penetration test. Crunch was used to generate the lists required while running a brute force attack. In this guide, we have learned how we can leverage various tools found on Kali Linux to effectively perform penetration testing.
