Beware: Certain PyPI Python Packages Pose Risks of Depleting Your Crypto Wallets
BLOGS


Security analysts have uncovered a series of seven packages hosted on the Python Package Index (PyPI) repository designed to pilfer BIP39 mnemonic phrases utilized for recovering private keys of cryptocurrency wallets.
Termed BIPClip by ReversingLabs, this campaign in the software supply chain attack domain saw these packages downloaded a collective 7,451 times before their removal from PyPI. The roster of packages includes:
1. jsBIP39-decrypt (126 downloads)
2. bip39-mnemonic-decrypt (689 downloads)
3. mnemonic_to_address (771 downloads)
4. erc20-scanner (343 downloads)
5. public-address-generator (1,005 downloads)
6. hashdecrypt (4,292 downloads)
7. hashdecrypts (225 downloads)
BIPClip, targeted at developers engaged in projects concerning the creation and safeguarding of cryptocurrency wallets, has been active since at least December 4, 2022, when hashdecrypt was initially introduced to the registry.
"This represents the latest instance of software supply chain attacks aimed at cryptocurrency assets," remarked security researcher Karlo Zanki in a report shared with The Hacker News. "It underscores the enduring appeal of cryptocurrency as a prime target for threat actors in the supply chain."
Demonstrating a level of caution to evade detection, one of the flagged packages, mnemonic_to_address, appeared devoid of malicious functions except for listing bip39-mnemonic-decrypt as its dependency, which housed the malicious component.
"Even if scrutinized for dependencies, the package's imported module and invoked function are meticulously selected to imitate legitimate functions, avoiding suspicion, given the numerous cryptographic operations in BIP39 standard implementations," elucidated Zanki.
This particular package is engineered to siphon off mnemonic phrases and relay the data to a server controlled by threat actors.
Additionally, two other packages highlighted by ReversingLabs – public-address-generator and erc20-scanner – operate similarly, with the former acting as bait to transmit the mnemonic phrases to the same command-and-control (C2) server.
In contrast, hashdecrypts functions distinctively, not as a pair, and contains nearly identical code internally to harvest the data.
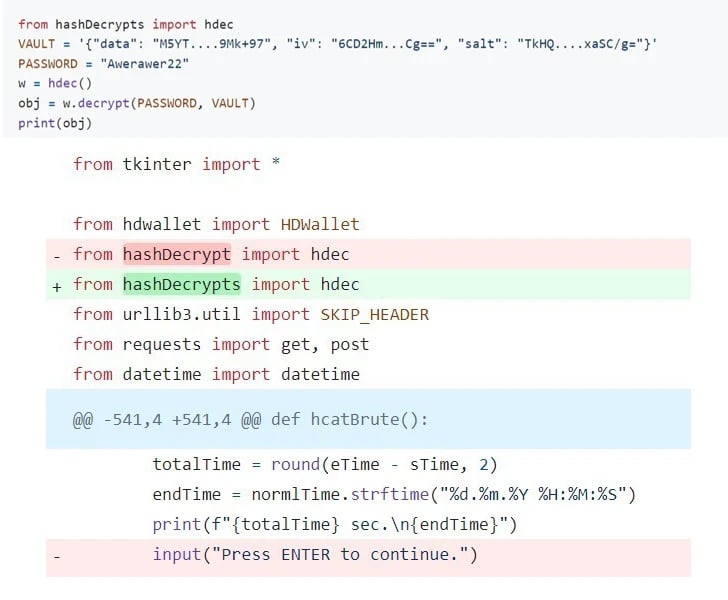
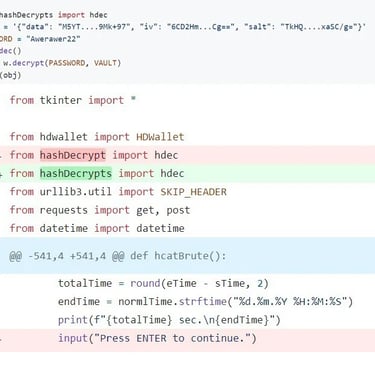
According to the software supply chain security firm, the package contains references to a GitHub profile under the name "HashSnake." This profile hosts a repository named hCrypto, advertised as a tool for extracting mnemonic phrases from crypto wallets using the hashdecrypts package.
A thorough examination of the repository's commit history reveals that the campaign has been ongoing for over a year. This is evident from the fact that one of the Python scripts initially imported the hashdecrypt package (without the "s") until March 1, 2024, coinciding with the upload date of hashdecrypts to PyPI.
It's notable that the threat actors associated with the HashSnake account maintain a presence on platforms like Telegram and YouTube to promote their illicit activities. This includes the release of a video on September 7, 2022, showcasing a tool called xMultiChecker 2.0 for checking crypto logs.
Security researcher Zanki remarked, "Each of the discovered packages was meticulously crafted to appear less suspicious. They were primarily focused on compromising crypto wallets and pilfering the contained cryptocurrencies. This narrow scope reduced the likelihood of detection by security and monitoring tools deployed within compromised organizations." These findings once again highlight the security risks present in open-source package repositories. Legitimate services such as GitHub are exploited as channels for distributing malware.
Moreover, abandoned projects have become an attractive target for threat actors to hijack developer accounts and release trojanized versions, potentially leading to widespread supply chain attacks.
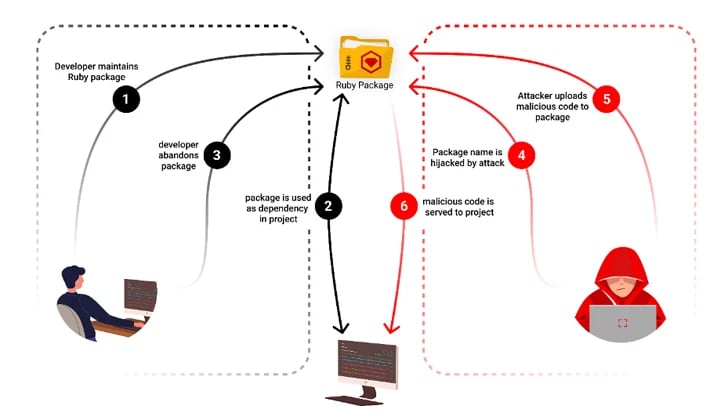
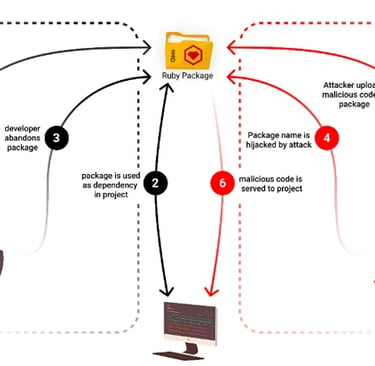
"Recent observations from Checkmarx emphasize that abandoned digital assets are not mere remnants of history; rather, they represent potential hazards waiting to explode, with attackers exploiting them more frequently, turning them into covert threats within open-source ecosystems."
"The incidents of MavenGate and CocoaPods serve as prime examples, demonstrating how abandoned domains and subdomains can be commandeered to deceive users and propagate malicious activities."
