Akira Ransomware Gang Extorts $42 Million; Now Targets Linux Servers
BLOGS


The Akira ransomware group has amassed approximately $42 million in illicit profits by breaching the networks of over 250 victims as of January 1, 2024.
According to a joint alert issued by cybersecurity agencies from the Netherlands and the U.S., along with Europol's European Cybercrime Centre (EC3), Akira ransomware has been targeting a wide range of businesses and critical infrastructure entities in North America, Europe, and Australia since March 2023.
Initially focusing on Windows systems, the Akira threat actors shifted to a Linux variant targeting VMware ESXi virtual machines in April 2023.
The group has evolved its tactics, starting with a C++ variant of the locker and later switching to a Rust-based code as of August 2023. It's important to note that this e-crime actor is distinct from the Akira ransomware family that was active in 2017.
To gain initial access to target networks, Akira actors exploit known vulnerabilities in Cisco appliances, such as CVE-2020-3259 and CVE-2023-20269. They also use Remote Desktop Protocol (RDP), spear-phishing, valid credentials, and virtual private network (VPN) services lacking multi-factor authentication (MFA) protections.
Akira actors employ various techniques to establish persistence, including creating a new domain account on the compromised system and abusing the Zemana AntiMalware driver to terminate antivirus-related processes using a Bring Your Own Vulnerable Driver (BYOVD) attack.
To escalate privileges, the adversary uses credential scraping tools like Mimikatz and LaZagne, while Windows RDP is used to move laterally within the victim's network. Data exfiltration is carried out using FileZilla, WinRAR, WinSCP, and RClone.
The ransomware encrypts targeted systems using a hybrid encryption algorithm combining Chacha20 and RSA. Additionally, the Akira ransomware binary includes a feature to inhibit system recovery by deleting shadow copies from the affected system.
In some cases, the group has deployed two distinct ransomware variants against different system architectures, namely Windows and ESXi encryptors (Akira_v2), during the same compromise event.
Blockchain and source code data suggest that the Akira ransomware group is likely affiliated with the now-defunct Conti ransomware gang. While a decryptor for Akira was released by Avast last July, it's highly likely that any vulnerabilities have since been addressed.
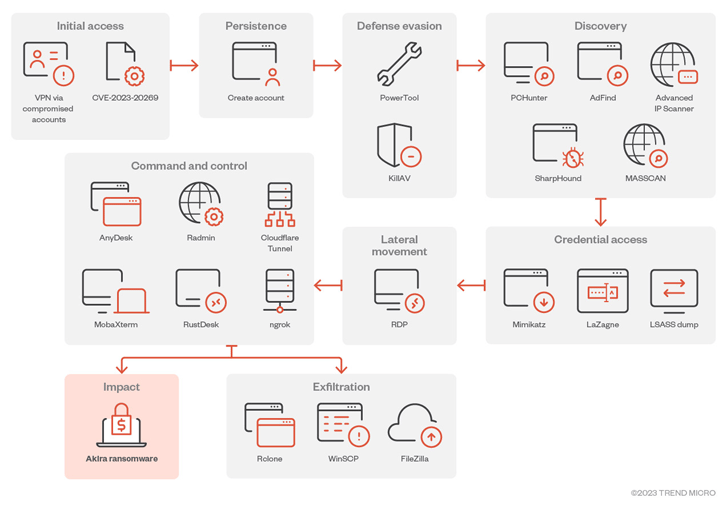
Akira's expansion to target Linux enterprise environments mirrors similar shifts made by other well-established ransomware groups, including LockBit, Cl0p, Royal, Monti, and RTM Locker.
LockBit's Struggles to Recover
This disclosure coincides with Trend Micro's revelation that the extensive law enforcement crackdown on the prolific LockBit gang in February significantly hampered the group's ability to rebound, leading it to fabricate old and false victim claims on its new data leak site.
"LockBit was among the most active and widely utilized Ransomware-as-a-Service (RaaS) variants, with potentially hundreds of affiliates, many of whom were associated with other prominent ransomware families," Chainalysis highlighted in February.
The blockchain analytics firm uncovered cryptocurrency transactions linking a LockBit administrator to a journalist in Sevastopol known as Colonel Cassad. This journalist has a history of soliciting donations for Russian militia group activities in the sanctioned regions of Donetsk and Luhansk following the start of the Russo-Ukrainian conflict in 2022.
It's noteworthy that in January 2022, Cisco Talos linked Colonel Cassad (also known as Boris Rozhin) to an anti-Ukraine disinformation campaign orchestrated by the Russian state-sponsored group known as APT28.
"In the aftermath of the crackdown, LockBitSupp [the alleged leader of LockBit] seems to be attempting to inflate the number of apparent victims while also concentrating on publicizing victims from countries where law enforcement agencies participated in the disruption," Trend Micro revealed in a recent analysis.
"This may be an effort to reinforce the narrative that LockBit will return even stronger and target those responsible for its disruption."
During an interview with Recorded Future News last month, LockBitSupp acknowledged the temporary decline in profits but pledged to enhance their security measures and "continue operating as long as I am alive."
"Reputation and trust are crucial for attracting affiliates, and once these are lost, it becomes more challenging to regain them. Operation Cronos succeeded in targeting the most critical aspect of its business: its reputation," Trend Micro emphasized.
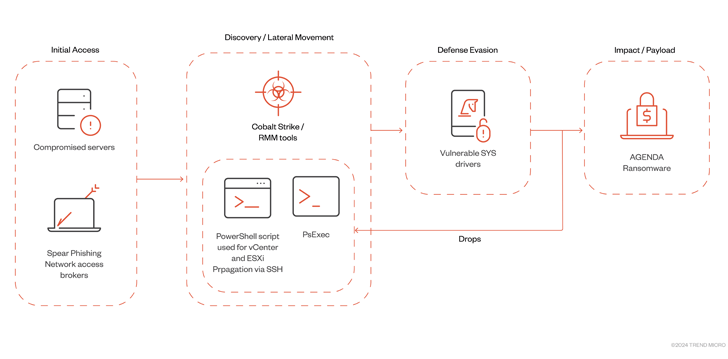
Agenda Returns with an Updated Rust Version#
The development also follows the Agenda ransomware group's (aka Qilin and Water Galura) use of an updated Rust variant to infect VMWare vCenter and ESXi servers through Remote Monitoring and Management (RMM) tools and Cobalt Strike.
"The Agenda ransomware's ability to spread to virtual machine infrastructure shows that its operators are also expanding to new targets and systems," the cybersecurity company said.
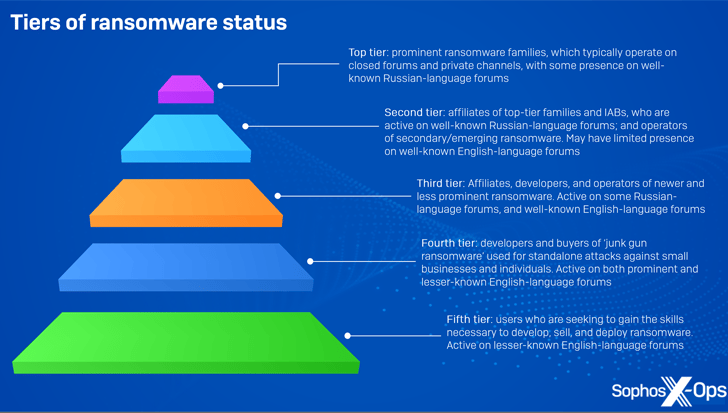
Even as a fresh crop of ransomware actors continues to energize the threat landscape, it's also becoming clearer that "crude, cheap ransomware" sold on the cybercrime underground is being put to use in real-world attacks, allowing lower-tier individual threat actors to generate significant profit without having to be a part of a well-organized group.
Interestingly, a majority of these varieties are available for a single, one-off price starting from as low as $20 for a single build, while a few others such as HardShield and RansomTuga are offered at no extra cost.
"Away from the complex infrastructure of modern ransomware, junk-gun ransomware allows criminals to get in on the action cheaply, easily, and independently," Sophos said, describing it as a "relatively new phenomenon" that further lowers the cost of entry.
"They can target small companies and individuals, who are unlikely to have the resources to defend themselves or respond effectively to incidents, without giving anyone else a cut."
