How Hashing Works
ARTICLES
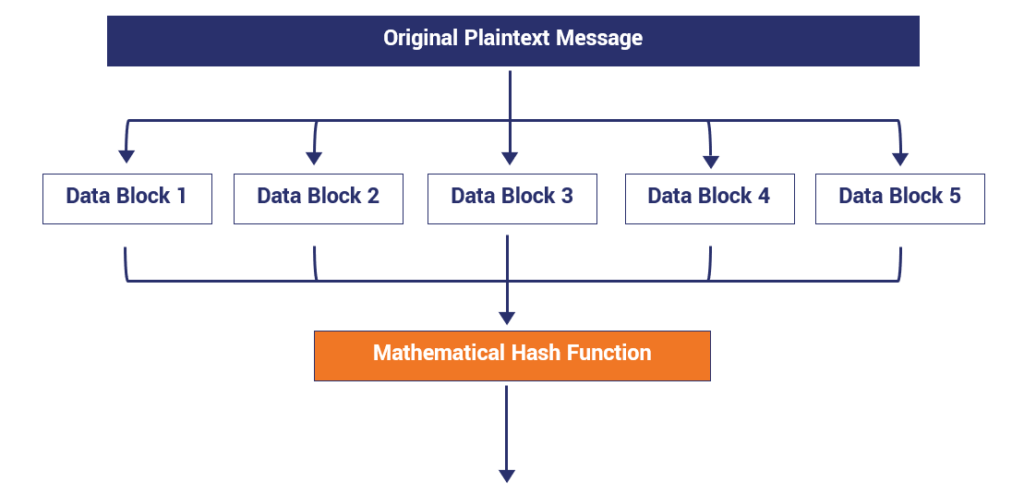
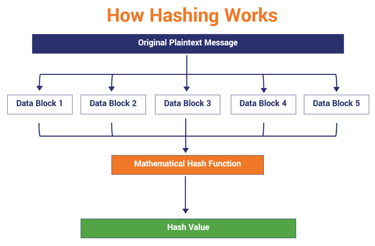
When people hear the word “hashing,” they often confuse it with encryption. That confusion causes a lot of problems, especially when learning cybersecurity. Hashing is not about hiding information so you can get it back later. Hashing is about turning information into a fixed fingerprint that proves something existed in a specific form.
So, the goal of this walkthrough is simple. By the end, you should understand what hashing really is, why it exists, and how it’s used in real systems, without needing any advanced math or cryptography background.
STARTING WITH A SIMPLE IDEA
The easiest way to understand hashing is to think about fingerprints. If you and I both see the same person’s fingerprint, we know it came from the same finger. But we can’t look at a fingerprint and recreate the person’s hand exactly.
That’s what hashing does to data.
You take some input, like a password or a file, and the hashing process turns it into a fixed-looking output called a hash. If the input changes even slightly, the hash changes completely.
HASHING A SIMPLE WORD
Instead of talking about theory, it’s better to see it.
Let’s start with a very simple word and hash it using a common algorithm. I’ll explain what’s happening as we go.
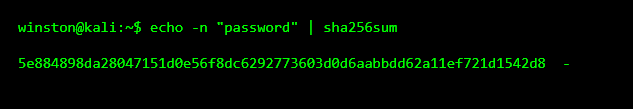
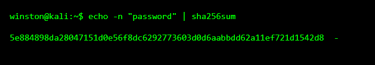
Here, the word "password" went in, and a long string of characters came out. That output is always the same for that exact input. Every time you hash the word "password" using SHA-256, you will get that exact result.
WHY THE OUTPUT LOOKS RANDOM
A lot of beginners ask why hashes look like random nonsense. A good hash algorithm is designed to spread information evenly. That means even small inputs produce outputs that look unpredictable.
This is intentional. If hashes were readable or patterned, attackers could guess inputs more easily.
WHAT HAPPENS IF THE INPUT CHANGES A LITTLE
Now let’s change the input just slightly and see what happens.
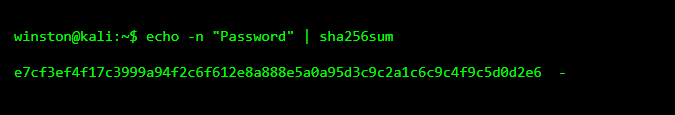
Notice how changing just one letter completely changed the hash. There is no visible relationship between the two outputs. This is one of the most important properties of hashing. Tiny changes in input cause massive changes in output.
WHY HASHES ARE ONE-WAY
This is where hashing is very different from encryption.
With encryption, you lock data and later unlock it with a key. With hashing, there is no key and no unlock process. Once data is hashed, it cannot be reversed back to the original input.
That’s why systems don’t store passwords directly. They store hashes instead.
HOW PASSWORD STORAGE REALLY WORKS
When you create a password on a website, the site does not store your actual password. Instead, it hashes the password and stores the hash.
Later, when you log in, the site hashes the password you typed and compares it to the stored hash. If they match, access is granted.
At no point does the system need to know your real password again.
SHOWING THIS COMPARISON IN PRACTICE
Let’s simulate this idea locally.
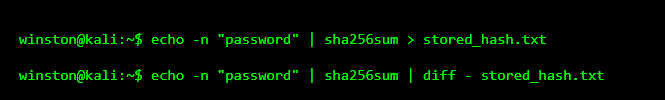
No output here means the hashes matched. That’s how systems verify passwords without ever storing them in plain text.
WHY YOU CAN’T JUST “DECODE” A HASH
A very common beginner question is why you can’t just reverse a hash. The reason is that hashing doesn’t store information in a reversible way. Many different inputs could theoretically produce the same length of output, but the algorithm makes it practically impossible to work backward.
The only way to “crack” a hash is to guess inputs, hash them, and compare the result. That’s not reversing. That’s guessing.
THIS IS WHERE HASH CRACKING COMES IN
When attackers crack hashes, they are not decoding them. They are guessing passwords, hashing those guesses, and checking if any match the target hash.
That’s why strong passwords matter. Longer and more complex inputs make guessing much harder.
WHY SALTS EXIST
One more important concept is salting. A salt is extra random data added to a password before hashing. This prevents attackers from using precomputed hash lists.
Even if two users have the same password, their hashes will look completely different when salts are used.
This is why modern systems always combine hashing with salts.
If there’s one thing to remember, it’s this. Hashing is not meant to be reversed. It’s meant to be compared. That single idea explains why hashing is everywhere in cybersecurity.
