How Hackers Exploit CCTV Cameras
ARTICLES


INTRODUCTION
CCTV cameras are installed to improve safety. People assume that once a camera is mounted and recording, the job is done. What many don’t realize is that modern CCTV systems are not just cameras. They are small computers connected to networks, running software, storing data, and responding to requests.
That makes them powerful tools for security, but also quiet points of failure when they are misconfigured or forgotten.
This walkthrough explains how CCTV cameras are commonly exploited in the real world, step by step, in a way that focuses on understanding rather than instruction.
THE FIRST MISTAKE PEOPLE MAKE
The biggest mistake with CCTV systems is treating them as physical devices instead of digital ones. Once a camera is plugged into a network, it becomes part of that network just like a laptop or a server. It listens for connections. It accepts commands. It stores data.
When those facts are ignored, cameras become one of the weakest points in an environment.
STEP 1: CAMERAS SHOW UP ON THE NETWORK
When someone gains access to a network, one of the first things they do is simply look around. Not to attack, but to understand what kinds of devices exist. Cameras tend to stand out because many of them come from the same vendor and share similar hardware fingerprints.
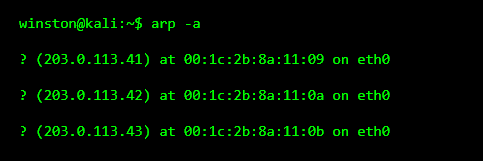
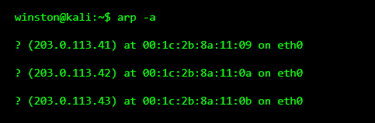
As you can see, nothing has been attacked here. This is just observation. Seeing multiple devices with nearly identical hardware signatures often points to embedded systems like cameras.
WHY CAMERAS ARE EASY TO MISS
Cameras are designed to stay on all the time. They are installed once and rarely touched again. Firmware updates are uncommon.
If someone accesses a camera quietly, there is usually no alert, and no sign anything is wrong.
STEP 2: IDENTIFYING A CAMERA INTERFACE
Most CCTV cameras expose a simple web interface used for viewing footage or adjusting settings. These interfaces are often old, basic, and unchanged for years.
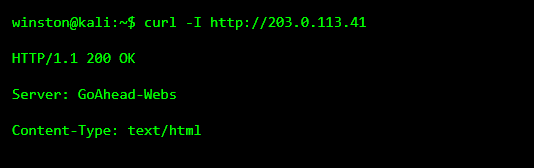
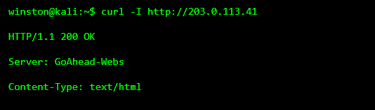
This response confirms the device is running a lightweight embedded web server commonly used by cameras. At this point, nothing has been forced or exploited. The device is simply responding.
STEP 3: DEFAULT TRUST IS THE REAL PROBLEM
Most CCTV breaches happen because cameras trust too much. Default credentials are left unchanged. Features meant for internal networks are exposed externally. Access controls are weak or misunderstood.
STEP 4: DISCOVERING AN OPEN STREAM
In many incidents, attackers never log in at all. They find that the camera is already willing to share video data without strong checks.
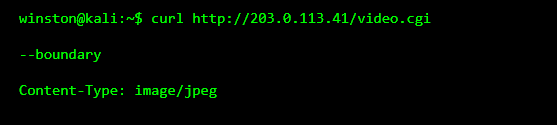
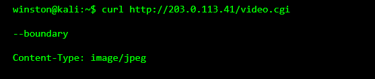
This means the camera is serving video data without verifying who is asking. That alone turns a security device into a liability.
STEP 5: THE MOMENT ACCESS IS CONFIRMED
Once a camera responds to requests it should not answer, the system crosses an important line. It moves from misconfigured to compromised.


There is no alert or warning. From the organization’s point of view, the camera is still working normally.
STEP 6: WHY THIS IS ALREADY SERIOUS
Even read-only access is dangerous. Cameras reveal physical layouts, movement patterns, schedules, and blind spots. Over time, this information becomes extremely valuable.
Nothing needs to be changed. Watching is enough.
STEP 7: ACCESSING STORED FOOTAGE
The situation escalates further when stored recordings become accessible. Many cameras store footage locally or on connected storage, often organized in simple directories.
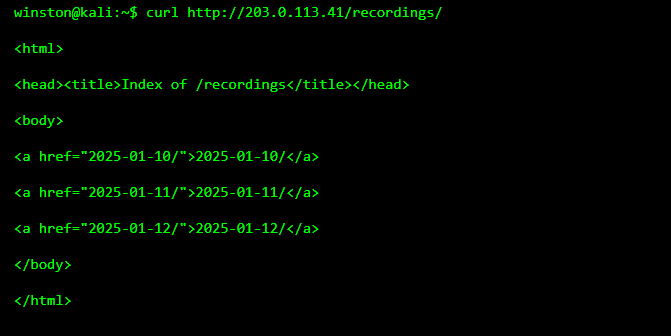
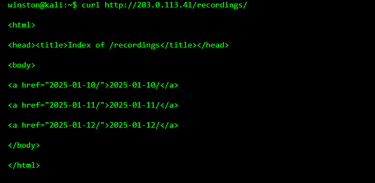
This confirms that historical footage is reachable.
STEP 8: STORED VIDEO LEAVES THE SYSTEM
Investigations often reveal that recordings were accessed and retrieved quietly, without triggering anything.
Stored footage reveals a lot of information.
WHY THIS OFTEN GOES UNDETECTED
Most CCTV systems do not log access in a way that security teams actively monitor. Even when logs exist, they are rarely reviewed unless something visibly breaks.
The camera keeps recording. The lights stay on. Everything appears normal.
THE UNCOMFORTABLE TRUTH
CCTV cameras are rarely attacked. They are inherited. They remain online, trusted, and forgotten long after the environment around them changes.
Attackers don’t need to break them. They just notice them.
