Hash Cracking
ARTICLES
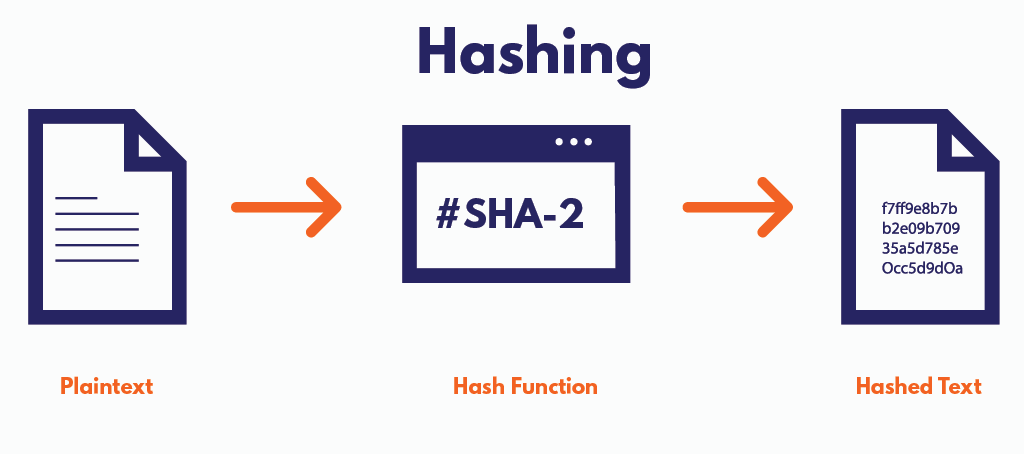
After learning how hashing works, the next question everyone asks is the same.
“If hashes can’t be reversed, how do hackers crack them?”
That question is important, because the answer clears up one of the biggest misunderstandings in cybersecurity. Hash cracking is not about undoing a hash. Nothing is being decrypted or reversed. What’s really happening is guessing, checking, and comparing.
So, in this walkthrough, I’m going to explain hash cracking the same way I explain it when teaching. Slowly, clearly, and in a way that actually makes sense.
STARTING WITH THE MOST IMPORTANT IDEA
The first thing to understand is this. A hash is not cracked by going backward. It’s cracked by guessing forward.
If I have a hash and I want to know the original password, the only thing I can do is guess a password, hash that guess, and see if it matches the hash I’m targeting. If it matches, I’ve found the password. If it doesn’t, I try another guess.
That’s it. There’s no shortcut.
SETTING UP A SIMPLE EXAMPLE
Let’s keep things realistic and simple.
Imagine we found a password hash in a database dump. We don’t know the password, only the hash. For this example, I’ll use a common hash so you can see how the process works.
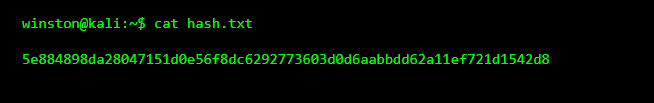
This hash might look meaningless, but earlier we saw that it’s the SHA-256 hash of the word password. We’re pretending we don’t know that yet.
WHAT HASH CRACKING ACTUALLY DOES
Before touching any tools, it’s important to understand the logic.
A cracking tool does three things over and over:
Take a word from a list
Hash it using the same algorithm
Compare the result to the target hash
If the two hashes match, the original word is found.
USING A WORDLIST
In real life, attackers don’t guess random words forever. They use wordlists. A wordlist is just a file containing thousands or millions of common passwords people tend to use.
This is why weak passwords are dangerous. Humans are predictable.
RUNNING A BASIC HASH CRACKING ATTEMPT
Now let’s walk through what this looks like in practice using a common tool. The goal here is understanding the output.
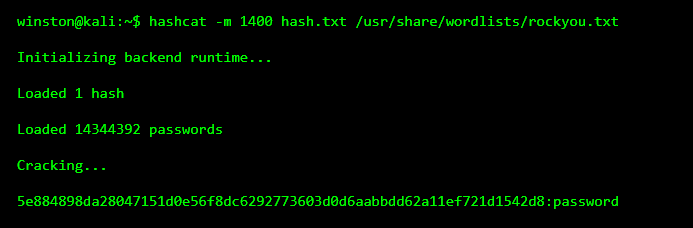
This output is the moment people misunderstand what just happened. The tool didn’t “reverse” the hash. It simply tried words from the list, hashed them, and one of those guesses matched.
The word "password" was in the wordlist, so it was found quickly.
WHY SOME HASHES CRACK INSTANTLY
Hashes crack fast when the password is common. Words like password, 123456, qwerty, or simple patterns are already known and already included in wordlists.
If a password is weak, cracking it is easy.
WHY STRONG PASSWORDS SLOW EVERYTHING DOWN
Now imagine the password was long, random, and never used before. That password would not be in a wordlist. The tool would have to guess endlessly, and in most cases, it would fail.
This is why password length matters more than complexity. The longer and more unique the password, the harder guessing becomes.
WHAT HAPPENS WITH SALTED HASHES
Earlier, we talked about salts. This is where they matter.
When a salt is added, the same password produces different hashes for different users. That means attackers can’t crack one hash and reuse the result everywhere. Each hash must be attacked individually.
Salting doesn’t make guessing impossible, but it makes it much slower and much more expensive.
WHY HASH CRACKING IS LOUD AND EXPENSIVE
Cracking hashes requires massive computing power. Every guess costs time and resources. That’s why defenders focus on slowing attackers down rather than stopping them entirely.
Strong hashing algorithms, salts, and long passwords turn cracking into a losing game.
PUTTING IT ALL TOGETHER
If you understand this, you understand hash cracking.
Nothing is decoded.
Nothing is reversed.
Everything is guessed.
Hash cracking only works when humans choose predictable passwords.
