CCTV Forensics
Investigating a Camera Breach After the Damage Is Done
ARTICLES


INTRODUCTION
When people think about CCTV security, they usually think about prevention. Strong passwords. Firewalls. Network segmentation. All of that matters, but in the real world, many investigations begin after something has already gone wrong.
A camera wasn’t supposed to be accessible. Footage wasn’t supposed to leave the system. Yet somehow, it did.
This is where forensics comes in. Not to guess what might have happened, but to carefully piece together what actually happened using evidence the system left behind.
STARTING WITH THE RIGHT MINDSET
Forensics is not about rushing to conclusions. It’s about slowing everything down. Instead of asking “who did this,” the better question is “what evidence exists.”
CCTV systems don’t behave like laptops or servers. Their logs are limited. Their storage is often basic. That means investigators have to work with whatever the camera was willing to record.
STEP 1: PRESERVING THE CAMERA STATE
The first thing done during a CCTV investigation is preserving the current state of the system. Not changing settings. Not rebooting unnecessarily.
Any changes risk destroying evidence.
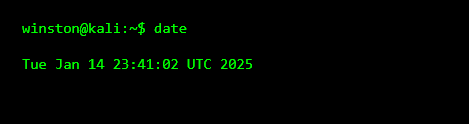
This timestamp matters. Every log and file will be compared against this moment.
STEP 2: CHECKING FOR MISSING OR ACCESSED FOOTAGE
One of the fastest indicators of compromise is missing or unexpectedly accessed recordings. Cameras usually store footage in predictable time-based structures.
Investigators look for gaps.
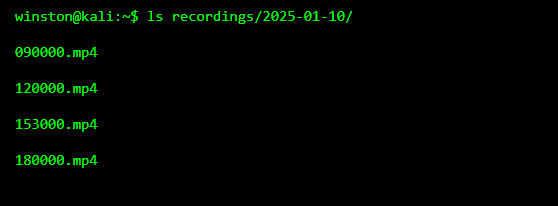
When footage exists consistently, investigators check access times next. Not just when files were created, but when they were last touched.
STEP 3: FILE METADATA TELLS A STORY
Even when footage hasn’t been deleted, file metadata can reveal whether it was accessed.


This matters because the access time doesn’t line up with normal usage. The camera recorded the file days earlier, but someone accessed it much later, at an unusual hour.
This doesn’t prove who accessed it, but it proves the footage was touched.
STEP 4: REVIEWING CAMERA LOGS
CCTV logs are often limited, but they still provide clues. Even basic logs can reveal connections, requests, or restarts.

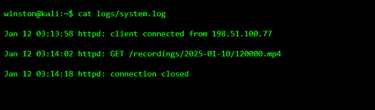
This is often the moment investigators pause. The timestamp matches the file access time. The log shows a request for a recording file.
That’s evidence.
STEP 5: CORRELATING TIMES AND EVENTS
Forensics is about connecting dots. The access time of the file, the log entry, and the system clock all line up.
This creates a clear event. A recording was retrieved remotely at a specific time.
Now the question changes from “did something happen” to “how did this connection exist.”
STEP 6: IDENTIFYING THE SOURCE OF ACCESS
The IP address in the logs doesn’t automatically identify a person, but it helps narrow the scope. Investigators compare it with firewall logs, router logs, or VPN records.

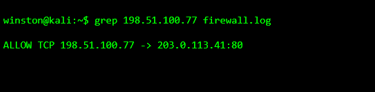
This confirms the connection wasn’t blocked. The camera was reachable and allowed the request.
STEP 7: UNDERSTANDING THE IMPACT
At this point, the investigation usually stops focusing on the camera and starts focusing on risk. What was visible in that footage. How long access existed. Whether other recordings were accessed.
WHY CCTV FORENSICS IS HARD
Cameras were never designed to support deep investigations. Logs are short-lived. Storage overwrites itself. Access tracking is minimal.
That’s why many CCTV incidents are discovered late, sometimes weeks or months after the first access.
