Analyzing a VENM File
Understanding Vendor Export Files in a Forensic Investigation
ARTICLES


INTRODUCTION
In real investigations, you don’t always get clean evidence like a hard drive image or a memory dump. Very often, especially with CCTV systems, access control panels, or industrial devices, you’re handed a strange file exported by the vendor’s software.
It might come with a name you’ve never seen before. One of those formats is a VENM file.
When people see a file like this, the first reaction is usually confusion. They don’t know what it contains, how to open it, or whether it’s even useful. This walkthrough explains how to approach a VENM file if you ever come across one.
WHAT A VENM FILE USUALLY IS
A VENM file is typically a vendor-generated export. It’s not raw video, not plain logs, and not a standard archive like ZIP. It’s often a container that holds recorded footage, metadata, timestamps, device identifiers, and sometimes internal logs, all bundled together in a proprietary way.
The important thing to understand is this. A VENM file is evidence. You don’t treat it like a normal file. You treat it like a sealed package.
STEP 1: PRESERVING THE FILE BEFORE TOUCHING IT
Before opening or modifying anything, the first thing done in forensics is preservation. That means confirming the file hasn’t been altered and documenting its state.
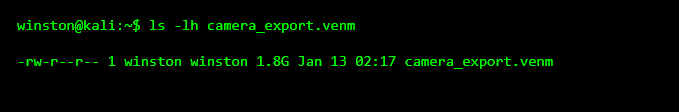
The size already tells us something. This isn’t a simple log file. It likely contains media or multiple data components.
STEP 2: CHECKING THE FILE TYPE WITHOUT OPENING IT
Next, the system is asked what it thinks the file is. This does not execute anything. It simply inspects the header.
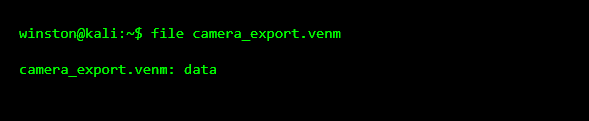
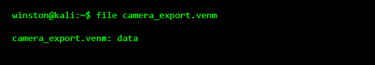
This is very common with proprietary formats. The operating system doesn’t recognize it because it’s not meant to be opened directly.
That doesn’t mean it’s useless. It just means we have to look deeper.
STEP 3: HASHING THE FILE FOR INTEGRITY
Before analysis continues, the file is hashed. This creates a digital fingerprint that proves the file wasn’t changed during the investigation.
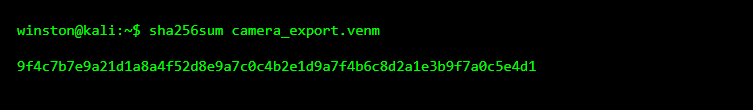
From this point on, any analysis must preserve this hash. If the hash changes, the evidence is no longer pristine.
STEP 4: LOOKING FOR STRUCTURE INSIDE THE FILE
Even proprietary files often contain readable strings. This doesn’t fully decode the file, but it can reveal clues about what’s inside.
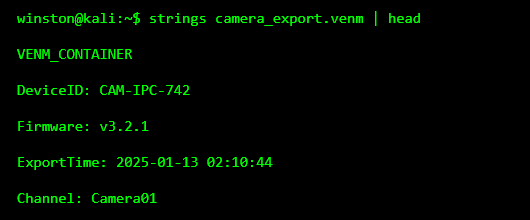
This is where the file starts talking. Without opening it in vendor software, we already know which device it came from, the firmware version, and when the export was created.
That metadata matters.
STEP 5: UNDERSTANDING WHAT THE EXPORT CONTAINS
VENM files usually bundle multiple components together. Recorded video, timestamps, event markers, and sometimes internal access logs are packaged so the vendor’s viewer can display them cleanly.
Forensics isn’t about rushing to view the footage. It’s about understanding context first.
Who created the export.
When it was created.
Which device produced it.
Those details help validate whether the file matches the incident timeline.
STEP 6: CHECKING FOR EMBEDDED FILE SIGNATURES
Even when a file is proprietary, it may contain standard formats inside it. Investigators look for recognizable headers.
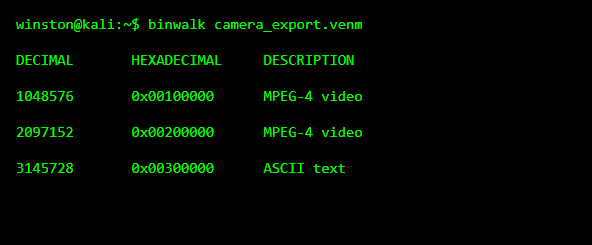
This confirms that the VENM file contains actual video streams and text data embedded inside it. It’s not just a wrapper. It’s a container.
STEP 7: WHY INVESTIGATORS USE VENDOR VIEWERS
At this point, many people want to extract everything manually. In practice, investigators often use the vendor’s official viewer in a controlled environment.
Why? Because the viewer understands how timestamps, playback speed, and event markers align. Raw extraction without context can lead to misinterpretation.
Forensics values accuracy over speed.
STEP 8: CORRELATING VENM DATA WITH OTHER EVIDENCE
A VENM file rarely stands alone. Its timestamps are compared with camera logs, firewall logs, and physical access records.
If footage shows movement at 03:14, investigators check whether logs show access around that same time.
WHAT A VENM FILE CAN PROVE
A VENM file can confirm that footage existed at a specific time, that it came from a specific device, and that it was exported at a specific moment.
It can also reveal gaps, missing segments, or inconsistencies that suggest footage was selectively exported.
That’s often more important than the video itself.
WHY VENM ANALYSIS IS IMPORTANT
Vendor formats are easy to dismiss because they feel unfamiliar. In reality, they are some of the most important artifacts in CCTV investigations because they combine media and metadata in one place.
Handled properly, they can stand up in court. Handled poorly, they can be challenged.
